2016-08-22 - BOLETO CAMPAIGN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-22-Boleto-campaign-infection-traffic.pcap.zip 1.3 MB (1,296,116 bytes)
- 2016-08-22-Boleto-campaign-infection-traffic.pcap (1,814,956 bytes)
- 2016-08-22-Boleto-campaign-spreadsheets.zip 2.6 kB (2,587 bytes)
- 2016-08-22-Boleto-campaign-email-tracker.csv (2,374 bytes)
- 2016-08-22-Boleto-campaign-malware-and-artifacts-info.csv (1,873 bytes)
- 2016-08-22-Boleto-campaign-emails-12-examples.zip 17.1 kB (17,095 bytes)
- 2016-08-22-Boleto-campaign-email-1205-UTC.eml (1,776 bytes)
- 2016-08-22-Boleto-campaign-email-1212-UTC.eml (1,811 bytes)
- 2016-08-22-Boleto-campaign-email-1213-UTC.eml (1,815 bytes)
- 2016-08-22-Boleto-campaign-email-1217-UTC.eml (1,835 bytes)
- 2016-08-22-Boleto-campaign-email-1226-UTC.eml (1,803 bytes)
- 2016-08-22-Boleto-campaign-email-1227-UTC.eml (1,838 bytes)
- 2016-08-22-Boleto-campaign-email-1236-UTC.eml (1,815 bytes)
- 2016-08-22-Boleto-campaign-email-1243-UTC.eml (1,834 bytes)
- 2016-08-22-Boleto-campaign-email-1248-UTC.eml (1,811 bytes)
- 2016-08-22-Boleto-campaign-email-1249-UTC.eml (1,851 bytes)
- 2016-08-22-Boleto-campaign-email-1318-UTC.eml (1,850 bytes)
- 2016-08-22-Boleto-campaign-email-1326-UTC.eml (1,799 bytes)
- 2016-08-22-Boleto-campaign-malware-and-artifacts-from-infected-host.zip 1.5 MB (1,496,253 bytes)
- Ionic.Zip.Reduced.dll (253,440 bytes)
- PSEXESVC.exe (189,792 bytes)
- VADER-PC.aes (16 bytes)
- VADER-PC.zip (1,079,289 bytes)
- VENC22082016yCXo92TVz0mndzIWH2SIwHAgsJZ1gncM.vbs (1,098 bytes)
- aaaaaaaaaaaa.xml (3,380 bytes)
- dll.dll.exe (396,480 bytes)
- gybxhaao.32w.vbs (343 bytes)
- hk4wmvwo.5bs.vbs (7,775 bytes)
- tmp51F8.tmpps1 (3,475 bytes)
- tmpAC55.tmp (11,548 bytes)
- tmpF103.tmp (11,548 bytes)
MY PREVIOUS DOCUMENTATION ON THIS CAMPAIGN:
- 2016-08-19 - Boleto campaign
- 2016-08-18 - Boleto campaign
- 2016-08-17 - Boleto campaign
- 2016-08-16 - Boleto campaign
- 2016-08-15 - Boleto campaign
- 2016-08-13 - Boleto campaign
- 2016-07-26 - Malspam hunt (one email at 2016-07-26 18:40 UTC)
- 2016-07-25 - Boleto campaign - Subject: Boleto de Cobranca - FIX - URGENTE
EMAILS
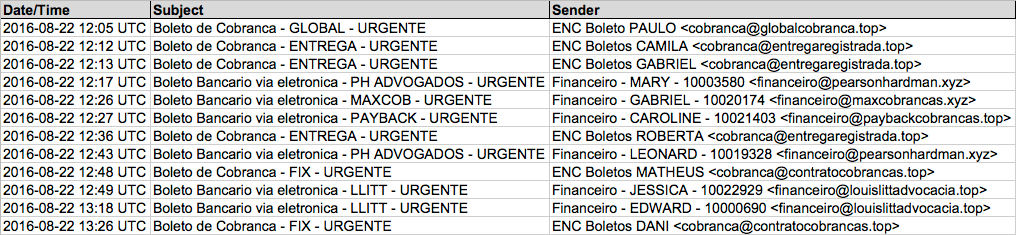
Shown above: Data from the spreadsheet (1 of 2).
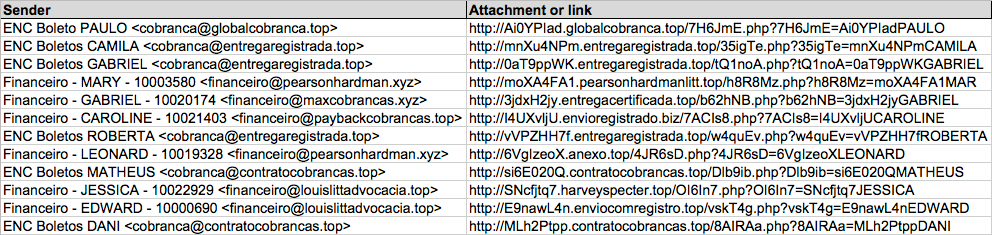
Shown above: Data from the spreadsheet (2 of 2).
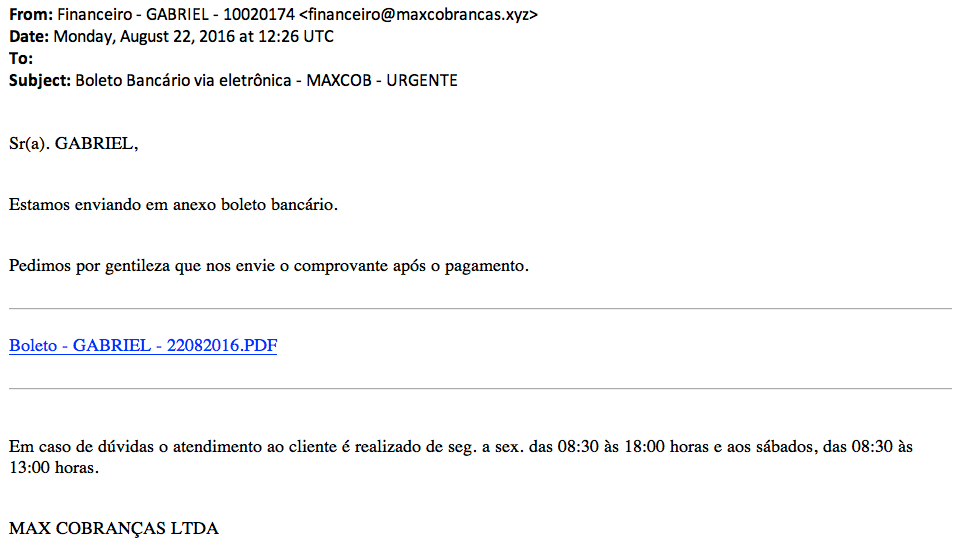
Shown above: Example of the emails.
EMAIL DETAILS
EXAMPLES OF SENDING EMAIL ADDRESSES:
- cobranca@contratocobrancas[.]top
- cobranca@entregaregistrada[.]top
- cobranca@globalcobranca[.]top
- financeiro@louislittadvocacia[.]top
- financeiro@maxcobrancas[.]xyz
- financeiro@paybackcobrancas[.]top
- financeiro@pearsonhardman[.]xyz
EXAMPLES OF SUBJECT LINES:
- Boleto Bancario via eletronica - LLITT - URGENTE
- Boleto Bancario via eletronica - MAXCOB - URGENTE
- Boleto Bancario via eletronica - PAYBACK - URGENTE
- Boleto Bancario via eletronica - PH ADVOGADOS - URGENTE
- Boleto de Cobranca - ENTREGA - URGENTE
- Boleto de Cobranca - FIX - URGENTE
- Boleto de Cobranca - GLOBAL - URGENTE
DOMAINS FROM LINKS IN THE EMAILS:
- anexo[.]top
- contratocobrancas[.]top
- entregacertificada[.]top
- entregaregistrada[.]top
- enviocomregistro[.]top
- envioregistrado[.]biz
- globalcobranca[.]top
- harveyspecter[.]top
- pearsonhardmanlitt[.]top
TRAFFIC
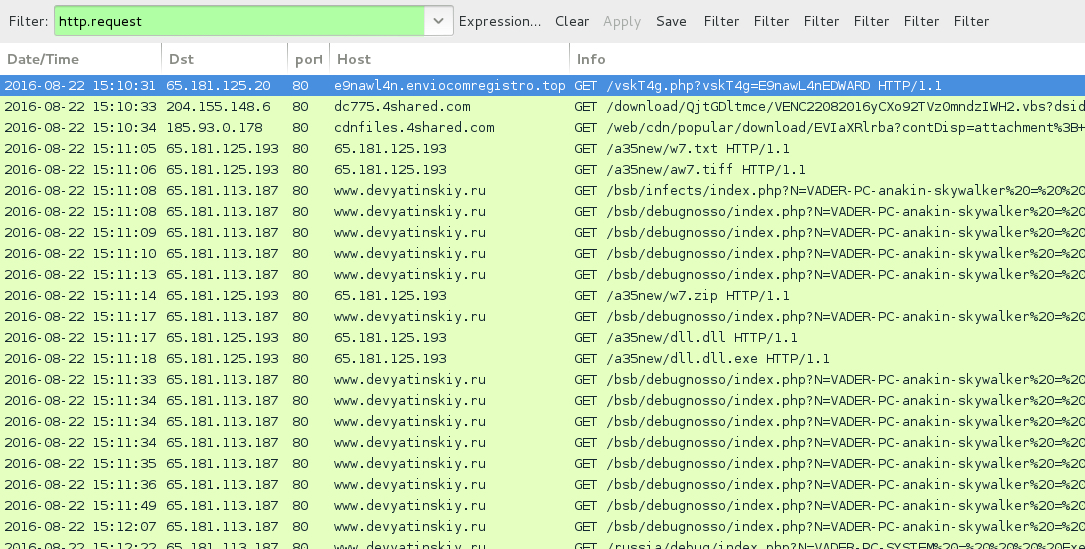
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- cdnfiles.4shared[.]com - VBS file from download link in the malspam
- 65.181.125[.]193 port 80 - 65.181.125[.]193 - GET /a35new/w7.txt
- 65.181.125[.]193 port 80 - 65.181.125[.]193 - GET /a35new/aw7.tiff
- 65.181.125[.]193 port 80 - 65.181.125[.]193 - GET /a35new/w7.zip
- 65.181.113[.]187 port 80 - www.devyatinskiy[.]ru - HTTP callback traffic
- 65.181.125[.]193 port 80 - 65.181.125[.]193 - GET /a35new/dll.dll
- 65.181.125[.]193 port 80 - 65.181.125[.]193 - GET /a35new/dll.dll.exe
- 65.181.113[.]204 port 443 - ssl.houselannister[.]top - IRC traffic (botnet command and control)
- imestre.danagas[.]ru - Response 192.64.147[.]142 - no follow-up UDP or TCP connection
- imestre.noortakaful[.]top - No response
- imestre.waridtelecom[.]top - No response
- imestre.aduka[.]top - No response
- imestre.saltflowinc[.]top - No response
- imestre.moveoneinc[.]top - No response
- imestre.cheddarmcmelt[.]top - No response
- imestre.suzukiburgman[.]top - No response
- imestre.houselannister[.]top - response: 127.0.0[.]1
- xxxxxxxxxxx.localdomain - No response
Click here to return to the main page.
