2017-07-18 - NEMUCODAES RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-18-NemucodAES-ransomaware-2-pcaps.zip 6.5 MB (6,456,378 bytes)
- 2017-07-18-1st-run-NemucodAES-ransomware-traffic.pcap (6,878,218 bytes)
- 2017-07-18-2nd-run-NemucodAES-ransomware-traffic.pcap (3,513,944 bytes)
- 2017-07-18-malspam-pushing-NemocodAES-ransomware-2-examples.zip 5.5 kB (5,538 bytes)
- 2017-07-17-UPS-themed-malspam-1840-UTC.eml (3,723 bytes)
- 2017-07-18-UPS-themed-malspam-1212-UTC.eml (3,781 bytes)
- 2017-07-18-malware-from-NemucodAES-ransomware-infections.zip 209.1 kB (209,146 bytes)
- 2017-07-18-1st-run-NemucodAES-PHP-script-retrieved-from-infected-host.txt (64,453 bytes)
- 2017-07-18-1st-run-NemucodAES-decryption-instructions.hta (1,705 bytes)
- 2017-07-18-1st-run-NemucodAES-javascript-returned-from-laurel.net.au.txt (148,574 bytes)
- 2017-07-18-2nd-run-NemucodAES-PHP-script-retrieved-from-infected-host.txt (64,419 bytes)
- 2017-07-18-2nd-run-NemucodAES-decryption-instructions.hta (1,705 bytes)
- 2017-07-18-2nd-run-NemucodAES-javascript-returned-from-xn--80aaumty_xn--p1ai.txt (148,565 bytes)
- UPS-Parcel-ID-4563806.doc.js (1,820 bytes)
- UPS-Parcel-ID-4563806.zip (1,516 bytes)
- UPS-Receipt-05395337.doc.js (1,802 bytes)
- UPS-Receipt-05395337.zip (1,504 bytes)
RELATED BLOG POSTS:
- malware-traffic-analysis.net - 2017-06-29: Kovter infection (link)
- malware-traffic-analysis.net - 2017-07-03: Kovter infection (link)
- malware-traffic-analysis.net - 2017-07-10: Kovter and Nemucod ransomware infection (link)
- Internet Storm Center (ISC) - 2017-07-14: NemucodAES and the malspam that distributes it (link)
TODAY'S NOTES:
- Today's UPS-themed malspam still has zip attachments containing .js files.
- No Kovter was seen today--only NemucodAES ransomware was downloaded by the extracted .js files.
- NemucodAES ransomware is all text-based script (JavaScript and PHP) and there is no post-infection traffic.
EMAILS
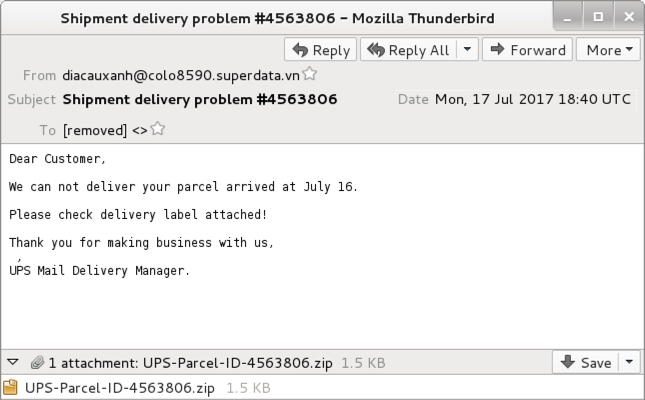
Shown above: Screenshot from an email (1 of 2).
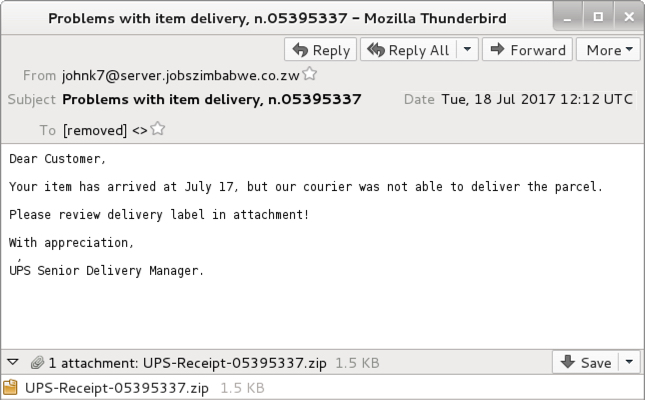
Shown above: Screenshot from an email (2 of 2).
EMAIL HEADERS:
- Date: Monday 2017-07-17 at 18:40 UTC
- From: diacauxanh@colo8590.superdata[.]vn
- Subject: Shipment delivery problem #4563806
- Attachment: UPS-Parcel-ID-4563806.zip
- Date: Tuesday 2017-07-18 at 12:12 UTC
- From: johnk7@server.jobszimbabwe[.]co[.]zw
- Subject: Problems with item delivery, n.05395337
- Attachment: UPS-Receipt-05395337.zip
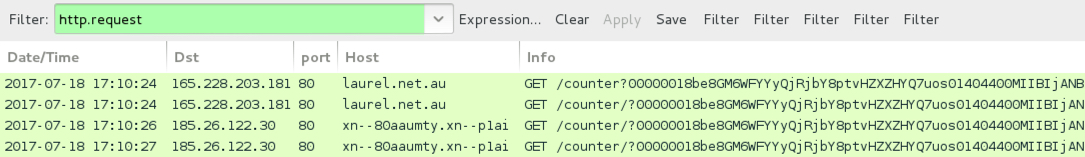
Shown above: Traffic from the 1st pcap filtered in Wireshark.
TRAFFIC
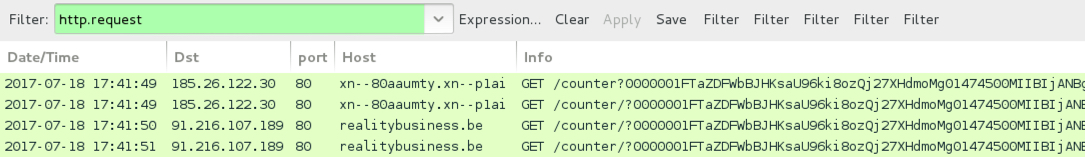
Shown above: Traffic from the 2nd pcap filtered in Wireshark.
PARTIAL URLS RECOVERED FROM THE .JS FILES:
- bandanamedia[.]com - GET /counter [followed by long string of characters]
- gimn5[.]by - GET /counter [followed by long string of characters]
- laurel[.]net[.]au - GET /counter [followed by long string of characters]
- realitybusiness[.]be - GET /counter [followed by long string of characters]
- www.proleite[.]com[.]pt - GET /counter [followed by long string of characters]
- xn--80aaumty[.]xn--p1ai - GET /counter [followed by long string of characters]
- xn---2016-gwea7d0alb0d[.]xn--p1ai - GET /counter [followed by long string of characters]
ONION DOMAINS FROM THE DECRYPTION INSTRUCTIONS:
- bgl3mwo7z3pqyysm[.]onion - GET /?[bitcoin address]
- bgl3mwo7z3pqyysm[.]onion[.]casa - GET /?[bitcoin address]
- bgl3mwo7z3pqyysm[.]onion[.]link - GET /?[bitcoin address]
- bgl3mwo7z3pqyysm[.]onion[.]to - GET /?[bitcoin address]
FILE HASHES
ZIP ATTACHMENTS:
- SHA256 hash: 24077e667fd317dafeba0d42628c479252602a091a7c5c3307f31de23daa2b4d
File size: 1,516 bytes
File name: UPS-Parcel-ID-4563806.zip
- SHA256 hash: 84ee93bdaa93a1cd19f65c3cc804f2e168f020f5f70ae2a0eb87bbf7cc4dea84
File size: 1,504 bytes
File name: UPS-Receipt-05395337.zip
EXTRACTED .JS FILES:
- SHA256 hash: 52ff1fa29675a6c55cab30d1dc0477c89b8f65e4e8b37ef56d2afc7c3058eac9
File size: 1,820 bytes
File name: UPS-Parcel-ID-4563806.doc.js
- SHA256 hash: a3d64b0a042eb778b04804d55e46be511f07449e77b5c05ee0d0ddced7aa9124
File size: 1,802 bytes
File name: UPS-Receipt-05395337.doc.js
IMAGES
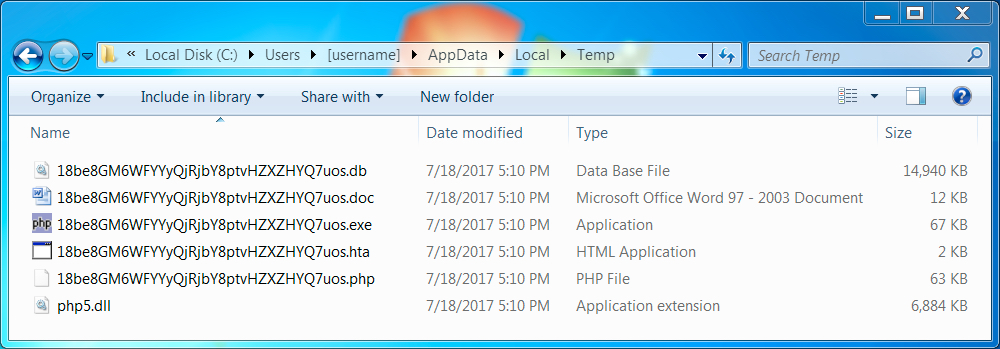
Shown above: Example of artifacts from an infected host.
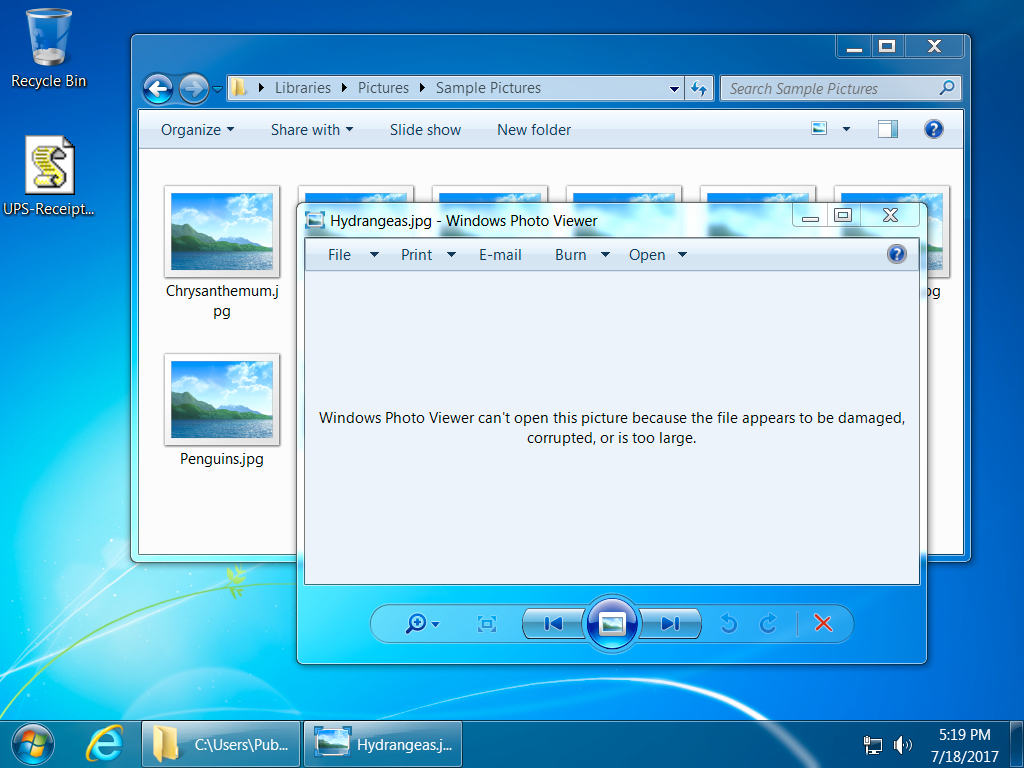
Shown above: File name extensions for the encrypted files do not change.
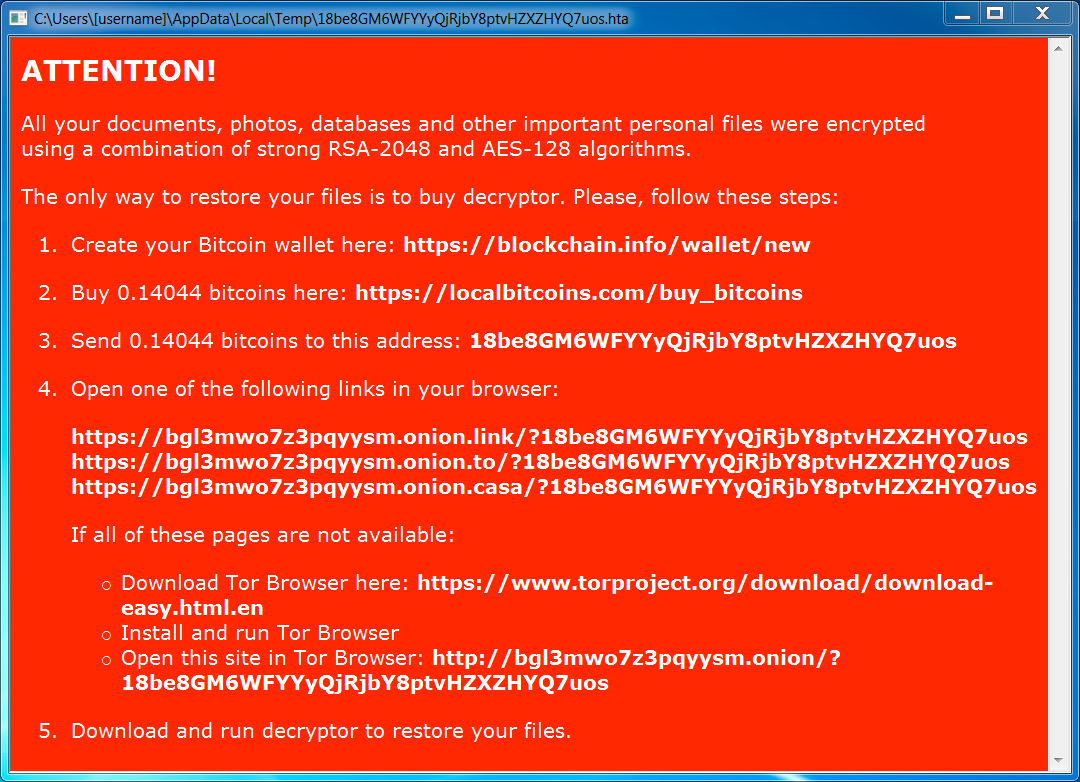
Shown above: Decryption instructions from the 1st infection.
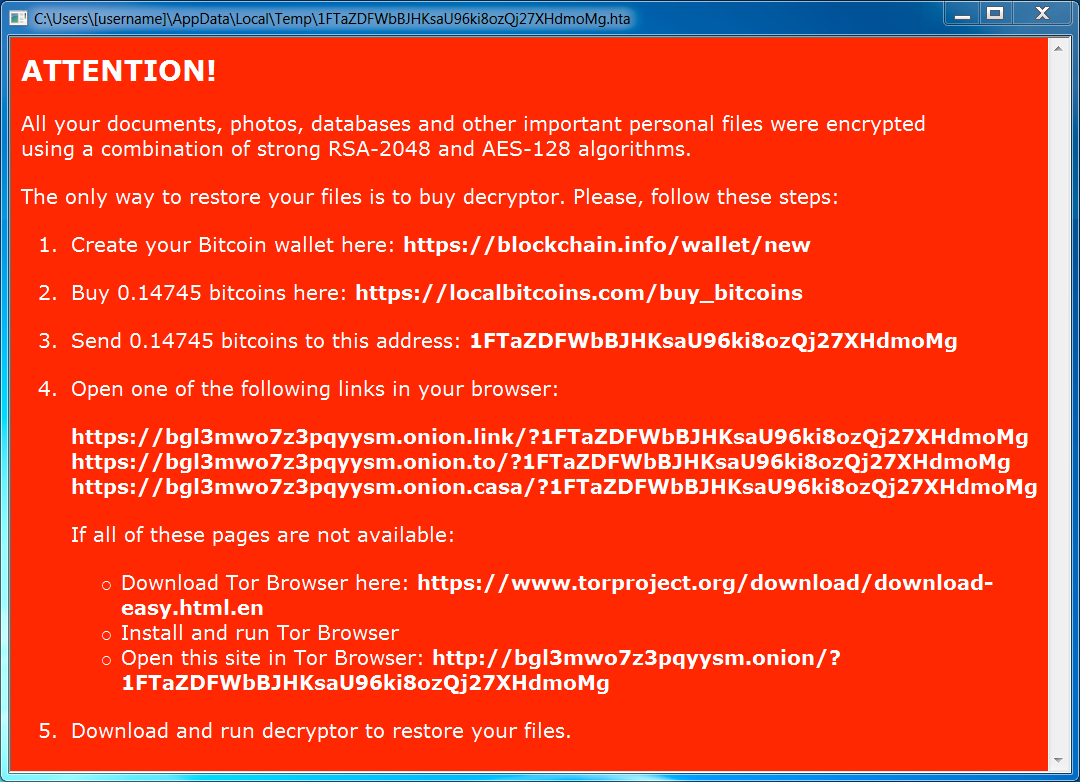
Shown above: Decryption instructions from the 2nd infection.
Shown above: You don't get anything more unless you pay the ransom.
Click here to return to the main page.
