2017-10-04 - BLANK SLATE CAMPAIGN PUSHES ".YKCOL" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-04-Blank-Slate-campaign-sends-Locky-ransomware-3-pcaps.zip 1.7 MB (1,691,013 bytes)
- 2017-10-04-Blank-Slate-malspam-tracker.csv.zip 1.0 kB (1,007 bytes)
- 2017-10-04-Blank-Slate-emails-and-Locky-ransomware-samples.zip 1.9 MB (1,855,745 bytes)
SOME BACKGROUND:
- 2017-03-02 - Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- 2017-03-22 - Internet Storm Center (ISC): "Blank Slate" malspam still pushing Cerber ransomware.
- 2017-06-29 - ISC: Catching up with Blank Slate: a malspam campaign still going strong.
- 2017-07-31 - Bleeping Computer: Crypt GlobeImposter Ransomware Distributed via Blank Slate Malspam.
- 2017-08-02 - Malware-Traffic-Analysis.net: "Blank Slate" malspam pushing Gryphon ransomware (a BTCware variant).
- 2017-09-11 - Malware-Traffic-Analysis.net: Blank Slate malspam pushes "Lukitus" variant Locky ransomware.
TODAY'S NOTES:
- Today's Blank Slate malspam is back to using double-zipped .js files as attachments.
- In my previous blog post on a 2017-09-15, the emails all had .doc attachments.
- Blank Slate is still pushing Locky ransomware, something also seen when I last documented it.
- Based on a Twitter conversation I had, these .js files might download other types of malware depending on your location.
EMAILS
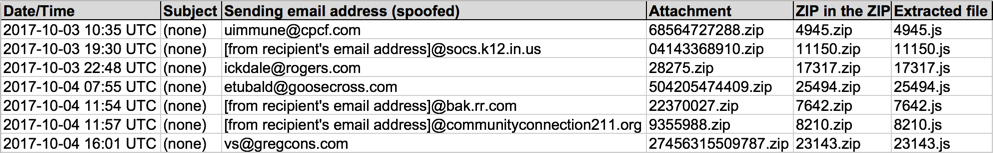
Shown above: Screenshot from the spreadsheet tacker.
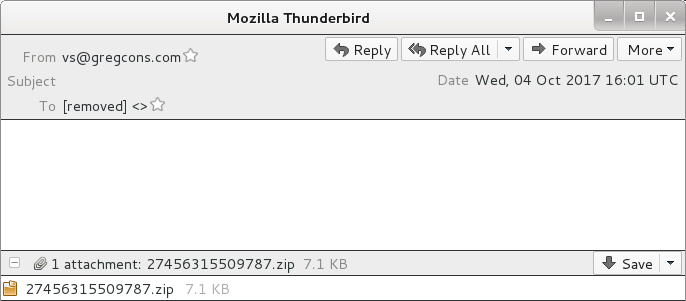
Shown above: Screen shot from one of the emails.
EMAILS COLLECTED:
- 2017-10-03 10:35 UTC -- Subject: (none) -- From (spoofed): uimmune@cpcf[.]com -- Attachment: 68564727288.zip
- 2017-10-03 19:30 UTC -- Subject: (none) -- From (spoofed): [from recipient's email address]@socs.k12[.]in[.]us -- Attachment: 04143368910.zip
- 2017-10-03 22:48 UTC -- Subject: (none) -- From (spoofed): ickdale@rogers[.]com -- Attachment: 28275.zip
- 2017-10-04 07:55 UTC -- Subject: (none) -- From (spoofed): etubald@goosecross[.]com -- Attachment: 504205474409.zip
- 2017-10-04 11:54 UTC -- Subject: (none) -- From (spoofed): [from recipient's email address]@bak.rr[.]com -- Attachment: 22370027.zip
- 2017-10-04 11:57 UTC -- Subject: (none) -- From (spoofed): [from recipient's email address]@communityconnection211[.]org -- Attachment: 9355988.zip
- 2017-10-04 16:01 UTC -- Subject: (none) -- From (spoofed): vs@gregcons[.]com -- Attachment: 27456315509787.zip
ATTACHMENT INFO:
- 28275.zip --> 17317.zip --> 17317.js
- 9355988.zip --> 8210.zip --> 8210.js
- 22370027.zip --> 7642.zip --> 7642.js
- 04143368910.zip --> 11150.zip --> 11150.js
- 68564727288.zip --> 4945.zip --> 4945.js
- 504205474409.zip --> 25494.zip --> 25494.js
- 27456315509787.zip --> 23143.zip --> 23143.js
TRAFFIC
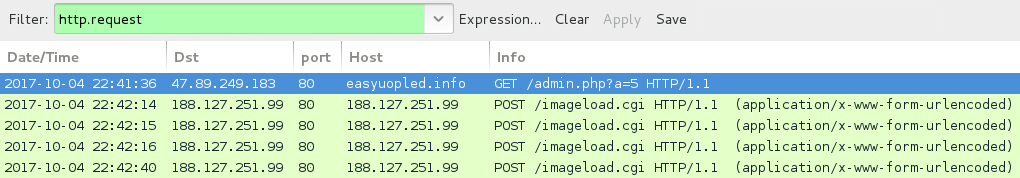
Shown above: Example of an infection traffic filtered in Wireshark (1 of 3).
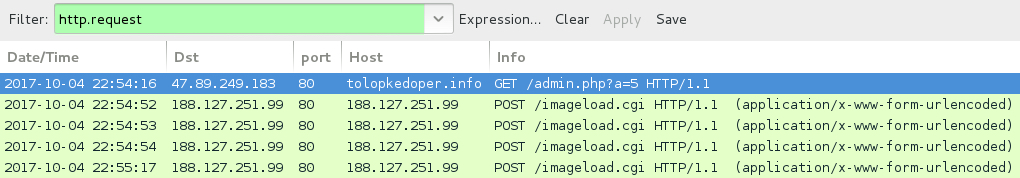
Shown above: Example of an infection traffic filtered in Wireshark (2 of 3).
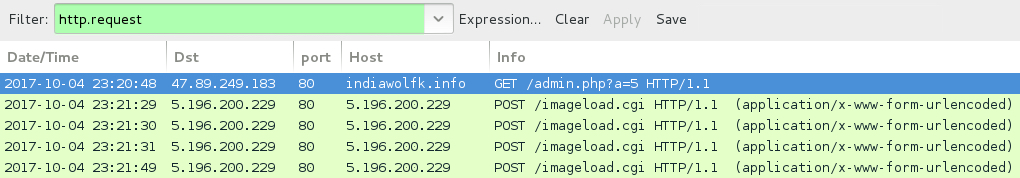
Shown above: Example of an infection traffic filtered in Wireshark (3 of 3).
TRAFFIC GENERATED BY .JS FILES TO DOWNLOAD LOCKY RANSOMWARE:
- 47.89.249[.]183 port 80 - easyuopled[.]info - GET /admin.php?a=5
- 47.89.249[.]183 port 80 - indiawolfk[.]info - GET /admin.php?a=5
- 47.89.249[.]183 port 80 - tolopkedoper[.]info - GET /admin.php?a=5
LOCKY RANSOMWARE POST-INFECTION TRAFFIC:
- 5.196.200[.]229 port 80 - 5.196.200[.]229 - GET /imageload.cgi
- 188.127.251[.]99 port 80 - 188.127.251[.]99 - GET /imageload.cgi
TOR DOMAIN FOR THE LOCKY DECRYPTOR (SAME ONE FOR A LONG TIME NOW):
- g46mbrrzpfszonuk[.]onion
ASSOCIATED FILES
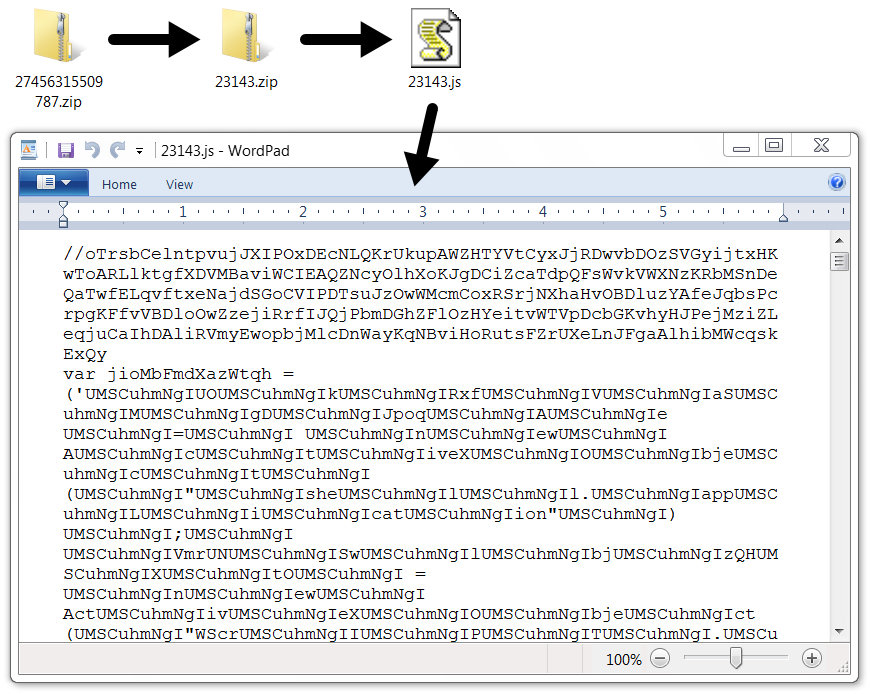
Shown above: One of the attached zip archives and its content.
ATTACHMENTS:
- cb83e413353adc40032d18eee14aeb2a4d4dd9c932a783fa91ce3672593f6091 - 28275.zip
- 8bdb3a3dba069a13445e932462699c5476565ed214d0bc07ef2f4d00d1f02695 - 9355988.zip
- e8ccf4520912e7f907288fa7ac01277d745bbf620a80f783648c098a05e91674 - 22370027.zip
- 2a8410765eb47633890371f93d1e06fd4133e883aa68502b38268fb9e0beef70 - 04143368910.zip
- 4cebecb96bf8240bf9c88af4a36fa3871acce6d70855af9ad39d2dc9e54d91b2 - 68564727288.zip
- c83a255c155cea02a59d39102746c493f2bdbffe01621f3133e6e146503dbd13 - 504205474409.zip
- f64a1008ba0d879aa19ac0d2ad7997044e5bd36853d54bab7b76654f93e3e321 - 27456315509787.zip
EXTRACTED .JS FILES:
- eff322d92e0fe53f639aeb699d8e3b5f4bc0e6f7fd3af59b8991a3073bbf747d - 4945.js
- 96cde533c664e5bff6a52047aab33e3c55412899168300c923fce4c10a8ede01 - 7642.js
- a08de25f44abb2357b141a9a78a461f194754455eb1d23521001e1d71674a444 - 8210.js
- cc4275dc199a5898fee370c5916890b13f2cd7688eeae1ab53af58f0449afeee - 11150.js
- 01a59f7f2b43e5cb146c2e1ae8566fed38a432f2df6598445d0f8b9279d92c61 - 17317.js
- a5e7f440f7b183e21717f516552014c91db91a25d8604de5244f59d997f7a6f9 - 23143.js
- d9ef61295df88cdfe5df4e5737e55bb8fe5b4a1f0e7a3785f106d78c71b40cf5 - 25494.js
FOLLOW-UP MALWARE (LOCKY RANSOMWARE BINARIES):
- SHA256 hash: ee1aa3cef61735a372499319b56827378398ecd4d701b5bce3c3bf62537289ed
File size: 594,944 bytes
File description: Locky ransomware from easyuopled[.]info on 2017-10-04.
- SHA256 hash: 5295bb51cd35e44162e5820793dfa5fa1f7be46677cf5f8f4490b12466058742
File size: 594,944 bytes
File description: Locky ransomware from indiawolfk[.]info and tolopkedoper[.]info on 2017-10-04.
LOCKY EXECUTED FROM THE LOCAL HOST AT:
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\60766.exe
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\74004.exe
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\188998.exe
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\468393.exe
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\667606.exe
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\779207.exe
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\870793.exe
IMAGES
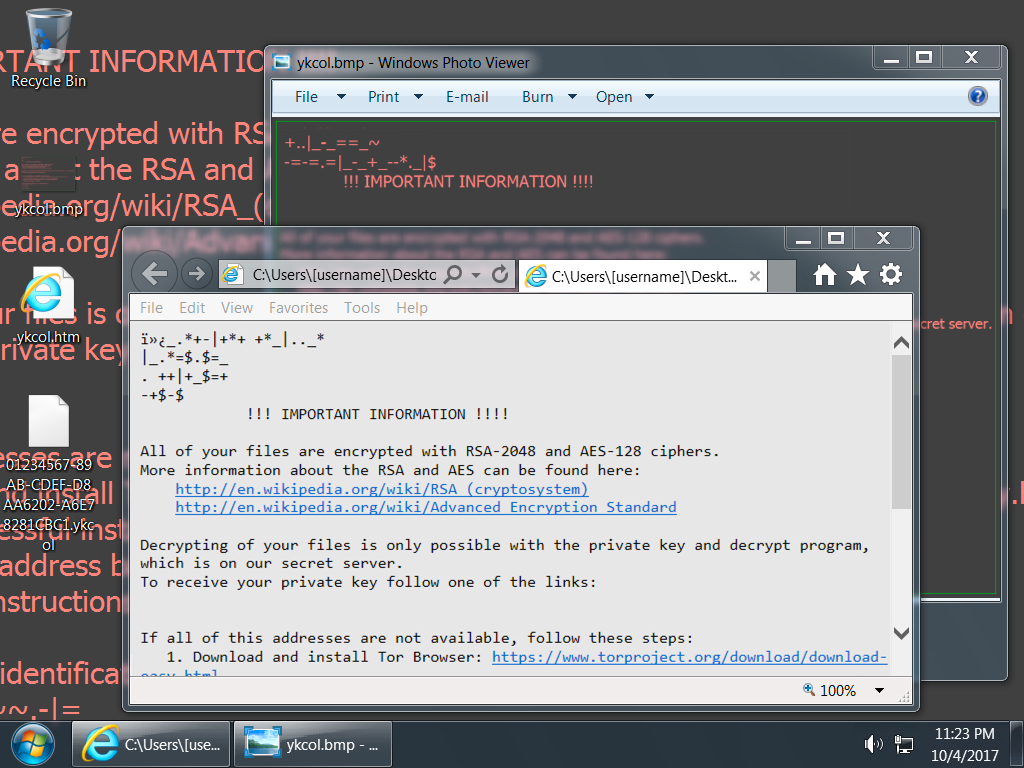
Shown above: Desktop of an infected Windows host.
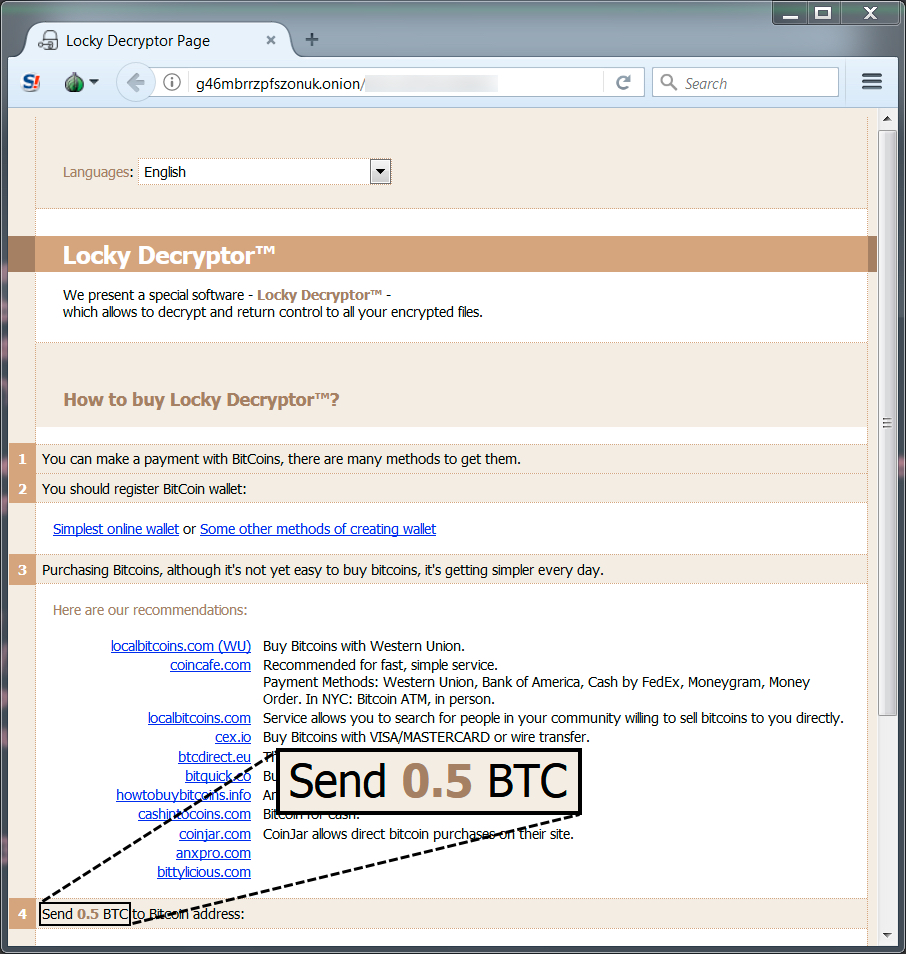
Shown above: The Locky decryptor showing today's ransom cost.
Click here to return to the main page.
