2014-05-26 - NUCLEAR EK FROM 192.243.115[.]146 - B631C84CiWS0DL.TEMENOPBG[.]RU & 3655320711-4.TEMENOPBG[.]RU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
SIMILAR BLOG ENTRIES:
- 2014-05-08 - Nuclear EK from 146.0.43[.]86 - denounce.verybutts[.]com - Original referer: asrv-a.akamaihd[.]net/sd/apps/fusionx/0.0.4.html?aff=1800-1005
- 2014-05-13 - Nuclear EK from 37.157.250[.]10 - full.409cremate[.]com - Original referer: gin.mapdiv[.]net/sd/apps/fusionx/0.0.4.html?aff=2040-2041
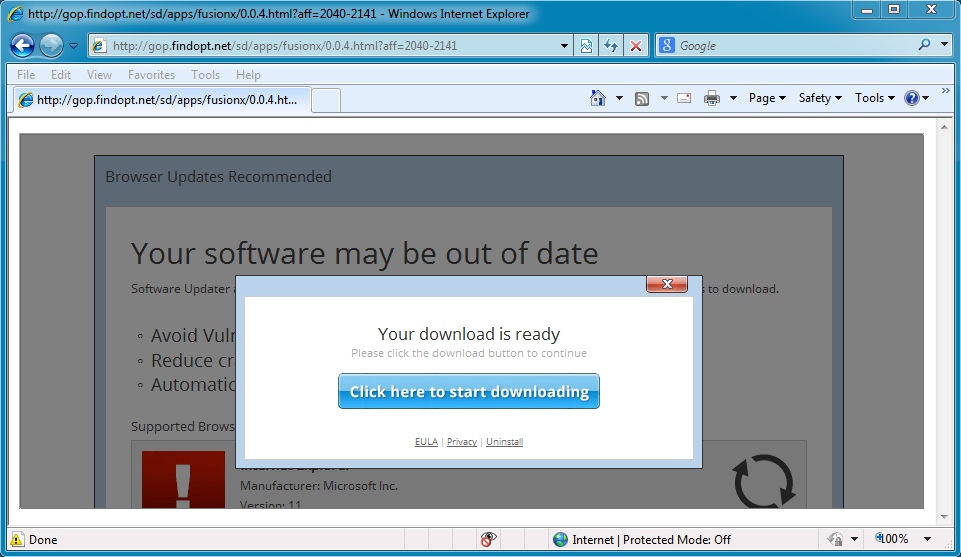
- 2014-05-16 - Nuclear EK from 37.157.250[.]13 - hospitality.medicalbodydonations[.]org - Original referer: gop.findopt[.]net/sd/apps/fusionx/0.0.4.html?aff=2040-2141
- 2014-05-26 - Nuclear EK from 192.243.115[.]146 - b631c84ciws0dl.temenopbg[.]ru & 3655320711-4.temenopbg[.]ru - Original referer: same as above
NOTES:
- Was curious if these ad URLs still generate Nuclear EK traffic, so I checked the last one from 2014-05-16, and it did.
- The infection chain remains the same as my previous entries (see above section), but the domain names have changed.
- Post-infection traffic shows callback requests similar to Asprox botnet malware.
CHAIN OF EVENTS
FAKE IE UPDATE PAGE AND REDIRECTS:
- 02:39:41 UTC - 174.37.233[.]13 - gop.findopt[.]net - GET /sd/apps/fusionx/0.0.4.html?aff=2040-2141
- 02:39:41 UTC - 174.37.233[.]13 - gop.findopt[.]net - GET /sd/apps/fusionx/0.0.4.js
- 02:39:41 UTC - 54.86.231[.]28 - www.ybpassbacks[.]com - GET /fusionx/www/delivery/afr.php?zoneid=1786&cb=23912495981
- 02:39:41 UTC - 54.86.231[.]28 - www.ybpassbacks[.]com - GET /fusionx/www/delivery/lg.php?bannerid=2091&[long string of characters]
- 02:39:42 UTC - 54.86.231[.]28 - www.ybpassbacks[.]com - GET /fusionx/www/delivery/ck.php?oaparams=2__bannerid=2091[long string of characters]
- 02:39:42 UTC - 78.47.182[.]238 - aus.lewisvilleoverheadgaragedoor[.]com - GET /assets/js/jquery-1.4.4.min.js?ver=2.8.1899
NUCLEAR EK:
- 02:39:44 UTC - 192.243.115[.]146 - b631c84ciws0dl.temenopbg[.]ru - GET /
- 02:40:05 UTC - 192.243.115[.]146 - 3655320711-4.temenopbg[.]ru - GET /1401051000.jar
- 02:40:06 UTC - 192.243.115[.]146 - 3655320711-4.temenopbg[.]ru - GET /f/1401051000/2
- 02:40:08 UTC - 192.243.115[.]146 - 3655320711-4.temenopbg[.]ru - GET /f/1401051000/2/2
POST-INFECTION CALLBACK FROM SECOND MALWARE PAYLOAD:
- 02:40:13 UTC - 114.37.97[.]60 - preluner-ter[.]com - GET /b/shoe/1480
- 02:40:20 UTC - 46.187.117[.]175 - tarbus-coteh[.]com - GET /com-phocaguestbook-php-q98.74/jquery/
- 02:41:38 UTC - 46.187.117[.]175 - tarbus-coteh[.]com - GET /com-uniterevolution-php-k69.65/soft64.dll
- 02:41:50 UTC - 76.127.161[.]112 - joye-luck[.]com - GET /b/eve/9e781ccf2ba9ee5e1846b066
- 02:42:43 UTC - 37.193.48[.]182 - joye-luck[.]com - POST /b/opt/6C0CC1D2A568ED7E10B91FEF
- 02:42:44 UTC - 37.193.48[.]182 - joye-luck[.]com - GET /b/letr/D7E89B1575FCFF1DC02D0D8C
- 02:42:45 UTC - 37.193.48[.]182 - joye-luck[.]com - POST /b/opt/8A22A0C6C71ACA0772CB3896
- 02:43:02 UTC - 37.193.48[.]182 - joye-luck[.]com - POST /b/req/2AEF0C2480BCA34F356D51DE
- 02:43:23 UTC - 37.193.48[.]182 - joye-luck[.]com - POST /b/req/28A9983B549858CCE149AA5D
CLICK FRAUD TRAFFIC BEGINS:
- 02:43:24 UTC - 192.162.19[.]34 - username-search[.]com - GET /
- 02:43:24 UTC - 192.162.19[.]34 - perimeter-search[.]com - GET /
- 02:43:24 UTC - 192.162.19[.]34 - forest-search[.]com - GET /
- 02:43:24 UTC - 192.162.19[.]34 - documents-search[.]com - GET /
- 02:43:24 UTC - 192.162.19[.]34 - country-search[.]com - GET /
- 02:43:24 UTC - 192.162.19[.]34 - travels-search[.]com - GET /
- 02:43:24 UTC - 192.162.19[.]34 - travels-search[.]com - GET /
- 02:43:24 UTC - 192.162.19[.]34 - blues-search[.]com - GET /
- 02:43:24 UTC - 192.162.19[.]34 - blues-search[.]com - GET /
- 02:43:24 UTC - 192.162.19[.]34 - ecored-search[.]com - GET /
- 02:43:25 UTC - 192.162.19[.]34 - companies-search[.]com - GET /
ADDITIONAL NOTES:
- Saw the following DNS query that didn't resolve:
- 02:40:19 UTC - Standard query 0x02be A avenue.GROWERDIRECTROSES[.]COM
- 02:40:19 UTC - Standard query response 0x02be No such name
- The Malwr sandbox analysis of the second malware payload shows the same DNS query, but it also shows the following traffic HTTP:
- 208.115.105[.]47 - cats.GROWERDIRECTROSES[.]COM - POST /es/break.php
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
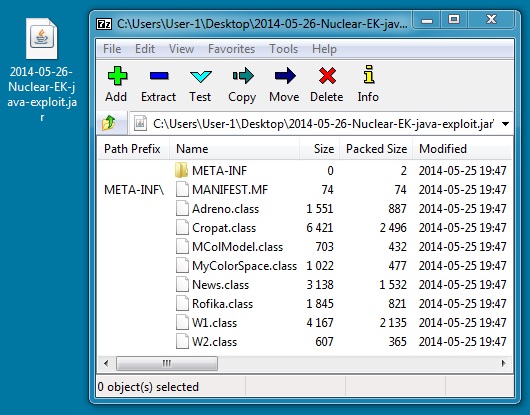
File name: 2014-05-26-Nuclear-EK-java-exploit.jar
File size: 10,419 bytes
MD5 hash: 443ce6291f701418353db118f6d08d27
Detection ratio: 0 / 52
First submission: 2014-05-26 03:36:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/b9eecbf110a75906eb89cb276edfe4ff731a889866849aafd43b9de84cf06e2d/analysis/
MALWARE PAYLOAD 1 OF 2
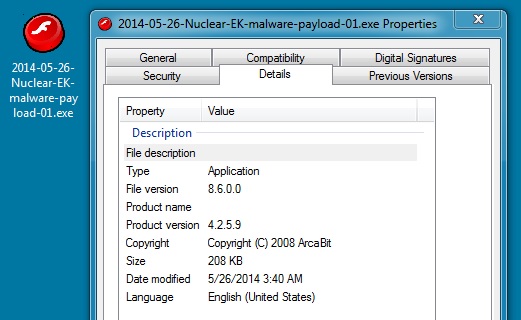
File name: 2014-05-26-Nuclear-EK-malware-payload-01.exe
File size: 213,736 bytes
MD5 hash: a929660981a45d8c349df13727ccd807
Detection ratio: 3 / 52
First submission: 2014-05-26 03:37:01 UTC
VirusTotal link: https://www.virustotal.com/en/file/a13a3362eab8fd1c24aad3c187cff0442a7230d518bf28c39e78fca7d691e78f/analysis/
MALWARE PAYLOAD 2 OF 2
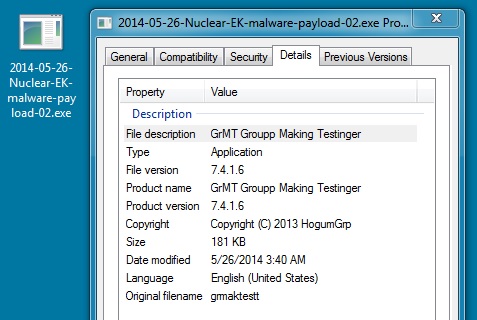
File name: 2014-05-26-Nuclear-EK-malware-payload-02.exe
File size: 185,856 bytes
MD5 hash: 6d9fd705920d01fa643b40512436f1aa
Detection ratio: 4 / 53
First submission: 2014-05-26 03:42:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/4ee55d2ff5ab6b27bd89524e8d53948ab31ccc2be9776bc6e5b8bb2c22a4bee5/analysis/
POST-INFECTION MALWARE DOWNLOADED
File name: UpdateFlashPlayer_070536b5.exe
File size: 203,065 bytes
MD5 hash: e9897f59508fe11860a749c46114a27a
Detection ratio: 10 / 52
First submission: 2014-05-26 03:43:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/5d3a3a48fe63445305fe8fd2151cd53f6411b54298bf51d86e54afe2648ce8cb/analysis/
ALERTS
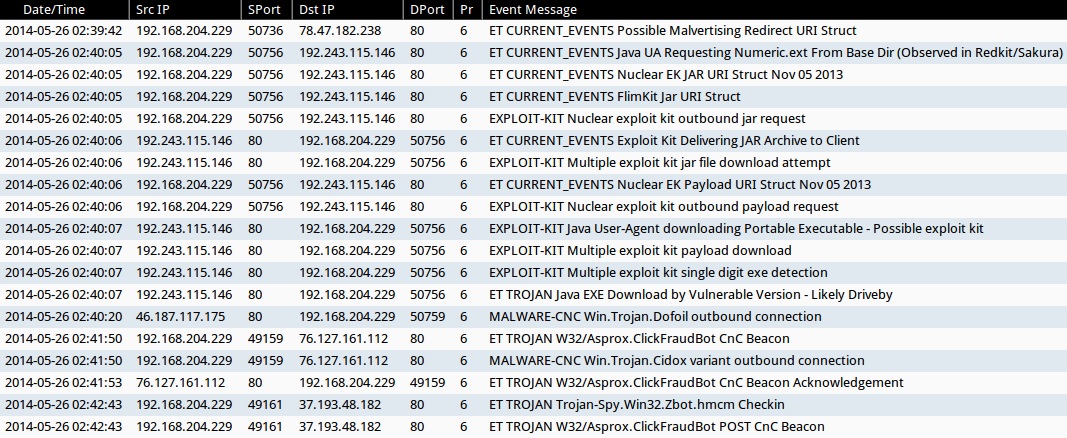
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion):
Emerging Threats ruleset
- 2014-05-26 02:39:42 UTC - 78.47.182[.]238:80 - ET CURRENT_EVENTS Possible Malvertising Redirect URI Struct (sid:2018454)
- 2014-05-26 02:40:05 UTC - 192.243.115[.]146:80 - ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura) (sid:2017199)
- 2014-05-26 02:40:05 UTC - 192.243.115[.]146:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 2014-05-26 02:40:05 UTC - 192.243.115[.]146:80 - ET CURRENT_EVENTS FlimKit Jar URI Struct (sid:2017152)
- 2014-05-26 02:40:06 UTC - 192.243.115[.]146:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 2014-05-26 02:40:06 UTC - 192.243.115[.]146:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 2014-05-26 02:40:07 UTC - 192.243.115[.]146:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
- 2014-05-26 02:41:50 UTC - 76.127.161[.]112:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 2014-05-26 02:41:53 UTC - 76.127.161[.]112:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-05-26 02:42:43 UTC - 37.193.48[.]182:80 - ET TROJAN Trojan-Spy.Win32.Zbot.hmcm Checkin (sid:2018437)
- 2014-05-26 02:42:43 UTC - 37.193.48[.]182:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
Sourcefire VRT ruleset
- 2014-05-26 02:40:05 UTC - 192.243.115[.]146:80 - EXPLOIT-KIT Nuclear exploit kit outbound jar request (sid:30219)
- 2014-05-26 02:40:06 UTC - 192.243.115[.]146:80 - EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
- 2014-05-26 02:40:06 UTC - 192.243.115[.]146:80 - EXPLOIT-KIT Nuclear exploit kit outbound payload request (sid:30220)
- 2014-05-26 02:40:07 UTC - 192.243.115[.]146:80 - EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit (sid:25042)
- 2014-05-26 02:40:07 UTC - 192.243.115[.]146:80 - EXPLOIT-KIT Multiple exploit kit payload download (sid:28593)
- 2014-05-26 02:40:07 UTC - 192.243.115[.]146:80 - EXPLOIT-KIT Multiple exploit kit single digit exe detection (sid:28423)
- 2014-05-26 02:40:20 UTC - 46.187.117[.]175:80 - MALWARE-CNC Win.Trojan.Dofoil outbound connection (sid:28809)
- 2014-05-26 02:41:50 UTC - 76.127.161[.]112:80 - MALWARE-CNC Win.Trojan.Cidox variant outbound connection (sid:29356)
Click here to return to the main page.