2015-01-13 - UPATRE/DYRE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-01-13-Upatre-Dyre-infection-traffic.pcap.zip
- 2015-01-13-malware-from-the-infection.zip
- 2015-01-13-Malwr-sandbox-analysis-of-Upatre.pcap.zip
RELATED REPORTING:
- https://blog.dynamoo.com/2015/01/malware-spam-johnsmithmail-irsgov-your.html
- https://community.spiceworks.com/t/your-tax-return-was-incorrectly-filled-out/370438
NOTES:
- The traffic uses jjencoding (link for details) before getting the malware zip file.
- The downloaded zip file from the link contains Upatre, and Upatre retrieves and runs Dyre.
- Previous Dyre campaigns I've documented:
- 2014-09-26 - Upatre infection with follow-up malware
- 2014-10-03 - Upatre infection with Dyre
- 2014-10-04 - Rig EK and Upatre from email links
- 2014-11-13 - Upatre/Dyre infection from email attachments
- 2014-12-05 - Upatre/Dyre infection
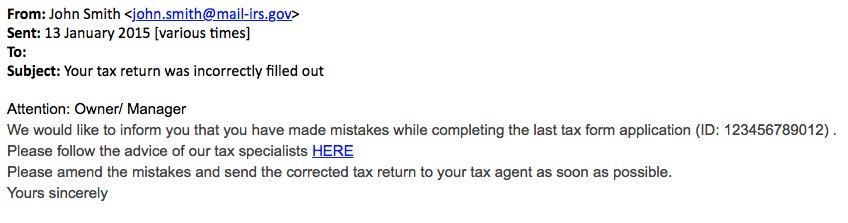
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
From: John Smith <john.smith@mail-irs[.]gov>
Sent: 13 January 2015 [various times]
To:
Subject: Your tax return was incorrectly filled out
Attention: Owner/ Manager
We would like to inform you that you have made mistakes while completing the last tax form application (ID: [12 digit number]) .
Please follow the advice of our tax specialists HERE
Please amend the mistakes and send the corrected tax return to your tax agent as soon as possible.
Yours sincerely
SOME LINKS FROM THE VARIOUS EMAILS:
jamjase[.]com - GET /taxadmin/get_doc.html
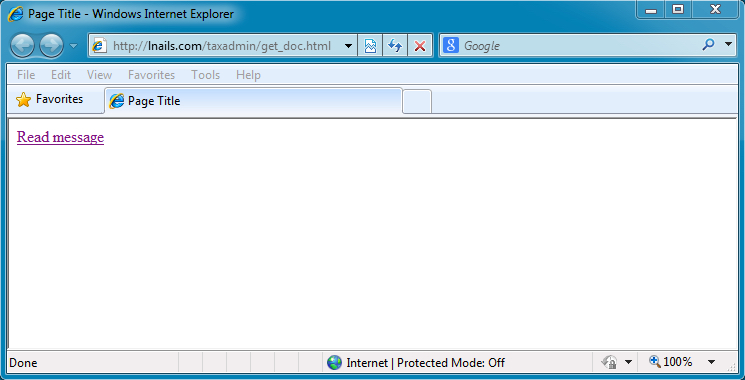
lnails[.]com - GET /taxadmin/get_doc.html
lsrj[.]in - GET /taxadmin/get_doc.html
monarchslo[.]com - GET /taxadmin/get_doc.html
omrdatacapture[.]com - GET /taxadmin/get_doc.html
prefeituraportoestrela[.]com - GET /taxadmin/get_doc.html
rfurniture[.]com - GET /taxadmin/get_doc.html
savoretti-ds[.]it - GET /taxadmin/get_doc.html
semiyun[.]com - GET /taxadmin/get_doc.html
serressabrevois[.]ca - GET /taxadmin/get_doc.html
solarbearrecords[.]com - GET /taxadmin/get_doc.html
INFECTION TRAFFIC
WHAT YOU WOULD SEE IF THE EMAIL LINK IS SUCCESSFUL:
TRAFFIC FROM THE INFECTED VM:
- 2015-01-13 15:23:40 UTC - 81.169.145[.]158 port 80 - lnails[.]com - GET /taxadmin/get_doc.html
- 2015-01-13 15:23:41 UTC - 74.118.68[.]160 port 80 - room.rd-webhosting[.]com - GET /js/jquery-1.14.94.js
- 2015-01-13 15:23:41 UTC - 217.78.1[.]156 port 80 - kerrydrivinglessons[.]com - GET /js/jquery-1.14.94.js
- 2015-01-13 15:23:42 UTC - 74.118.68[.]160 port 80 - room.rd-webhosting[.]com - GET /js/jquery-1.14.94.js?vnvKwhZI2QkRoQA=[user agent of web browser]
- 2015-01-13 15:23:43 UTC - 74.118.68[.]160 port 80 - room.rd-webhosting[.]com GET /js/jquery-1.14.94.js?get_message=889671283
- 2015-01-13 15:26:57 UTC - 202.153.35[.]133 port 19621 - 202.153.35[.]133:19621 GET /1301us23/WIN-C2KE6N4W3N1/0/61-SP1/0/
- 2015-01-13 15:26:58 UTC - 202.153.35[.]133 port 19621 - 202.153.35[.]133:19621 GET /1301us23/WIN-C2KE6N4W3N1/1/0/0/
- 2015-01-13 15:27:00 UTC - 141.8.195[.]84 port 80 - dstkom[.]com GET /mandoc/lit23.pdf
- 2015-01-13 15:27:19 UTC - 202.153.35[.]133 port 19623 - 202.153.35[.]133:19623 GET /1301us23/WIN-C2KE6N4W3N1/41/7/4/
- 2015-01-13 15:28:31 UTC - 95.211.156[.]95 port 443 - SSL/HTTPS traffic [several TCP sessions]
- 2015-01-13 15:28:46 UTC - 195.154.241[.]47 port 443 - SSL/HTTPS traffic [several TCP sessions]
- 2015-01-13 15:27:48 UTC - 77.72.174[.]163 port 3478 - UDP STUN traffic to: stun.voipbuster[.]com
- Malwr[.]com's analysis of the Upatre sample shows an additional HTTP request for: 216.251.43[.]17 - heritageonlineauctions[.]com - GET /mandoc/lit23.pdf
ALERTS FROM INFECTED VM
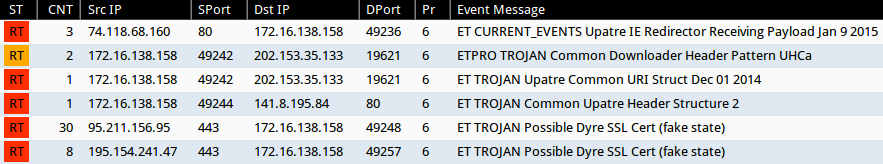
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 74.118.68[.]160 port 80 - ET CURRENT_EVENTS Upatre IE Redirector Receiving Payload Jan 9 2015 (sid:2020160)
- 202.153.35[.]133 port 19621 - ET TROJAN Upatre Common URI Struct Dec 01 2014 (sid:2019847)
- 202.153.35[.]133 port 19621 - ETPRO TROJAN Common Downloader Header Pattern UHCa (sid:2803270)
- 141.8.195[.]84 port 80 - ET TROJAN Common Upatre Header Structure 2 (sid:2018635)
- 95.211.156[.]95 port 443 ET TROJAN Possible Dyre SSL Cert (fake state) (sid:2019833)
- 195.154.241[.]47 port 443 - ET TROJAN Possible Dyre SSL Cert (fake state) (sid:2019833)
Talos (VRT) ruleset from Snort 2.9.7.0 on Debian 7 (not including preprocessor events):
- 74.118.68[.]160 port 80 - [1:27875:3] EXPLOIT-KIT Javascript obfuscation technique - has been observed in Rmayana/DotkaChef/DotCache exploit kit
- 217.78.1[.]156 port 80 - [1:27875:3] EXPLOIT-KIT Javascript obfuscation technique - has been observed in Rmayana/DotkaChef/DotCache exploit kit
- 74.118.68[.]160 port 80 - [1:32646:1] INDICATOR-COMPROMISE Potential malware download - _pdf.exe within .zip file
PRELIMINARY MALWARE ANALYSIS
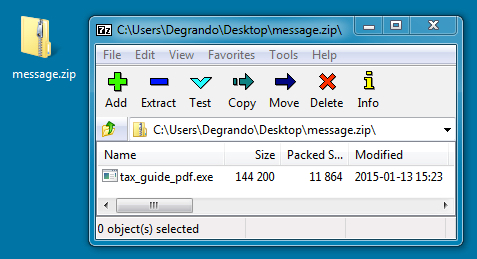
DOWNLOADED ZIP FILE:
File name: message.zip
EXTRACTED MALWARE (UPATRE):
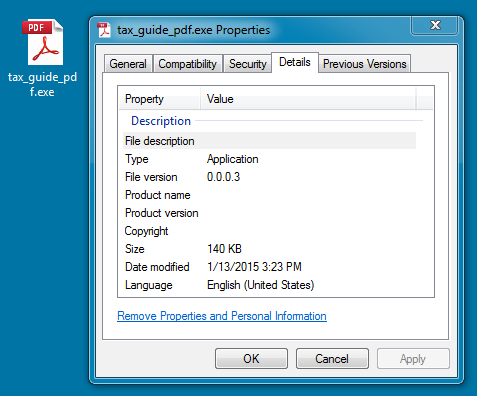
File name: tax_guide_pdf.exe
File size: 144,200 bytes
MD5 hash: d5b1370d307b788bc0bd23e744269eca
Detection ratio: 4 / 57
First submission: 2015-01-13 21:27:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/7e8cec257294080d9562fa671dffdbbcdb2ec6492421ece90ca7bb21cb9719f7/analysis/
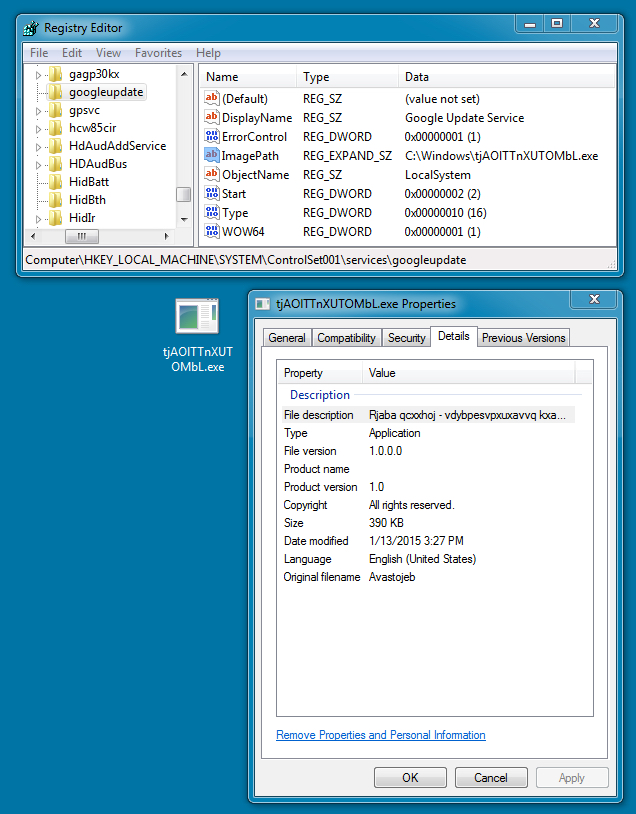
DROPPED MALWARE FOUND ON THE INFECTED VM (DYRE):
File name: C:\Windows\tjAOlTTnXUTOMbL.exe
File size: 399,872 bytes
MD5 hash: 7e7d8325dec4cc8c3244dd1c2d3c653a
Detection ratio: 10 / 57
First submission: 2015-01-13 15:00:32 UTC
VirusTotal link: https://www.virustotal.com/en/file/9cb95959bec83625a6cd9e2dd7d2261bc5715efb28124e600d9db357ea3912dc/analysis/
Click here to return to the main page.